It’s been roughly one month since rescope first got introduced and the feedback so far has been nothing but positive. Given that I was so new to twitter and everything, I didn’t know what to expect. Heck, with less than 20 followers at the time, I was surprised that anyone even saw the tweet, let alone click it. I dunno what happened, but somehow it gained some traction and before I knew, it was featured on pentester.land as the tool of the week! Let’s just say I wasn’t expecting that.
By the way, pentester.land is a fantastic resource for keeping up with the latest tools, articles, and writeups in the bugbounty world so definitely check that out if you haven’t.
I was planning on providing some background for this update but screw it, I’m just gonna cut to the chase. Without further ado, I’m excited to announce a new feature I’ve been working on which lets you define scopes directly from pretty much any public bug-bounty program.
Supported services
As with previous versions, no longer do you have to copy/paste the scope section to a file and set excludes manually. Just tell rescope which program you’d like to scope and it’ll take care of the rest.
$ rescope --burp -u hackerone.com/security -o importme.json
[-] Grabbing targets from hackerone.com/security
+ https://hackerone.com
+ https://api.hackerone.com
+ *.vpn.hackerone.net
+ https://hackerone-us-west-2-production-attachments.s3-us-west-2.amazonaws.com/
+ https://www.hackerone.com
+ https://errors.hackerone.net
+ https://*.hackerone-ext-content.com
+ https://ctf.hacker101.com
+ https://*.hackerone-user-content.com/
+ 66.232.20.0/23
+ 206.166.248.0/23
- https://support.hackerone.com
- https://ma.hacker.one
- https://www.hackeronestatus.com/
- https://info.hacker.one/
- https://go.hacker.one
[-] Parsing to JSON (Burp Suite)
[✓] Done. Wrote 185786 bytes to importme.json
As before, rescope does some regexp magic behind the scenes and what you get is a file that can be imported directly from Burp or ZAP (depending on your choice). For bug-hunters, this makes scoping extremely easy. See Github for instructions on how to import.
Result after importing
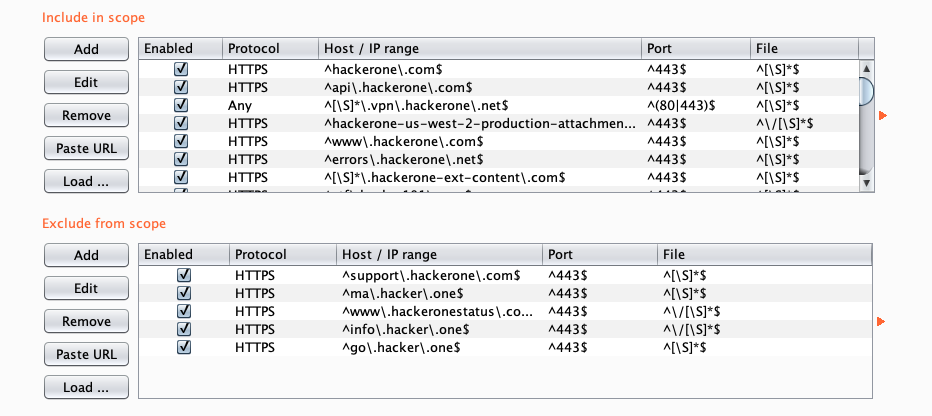
Fancy working on multiple programs at the same time? Why not stack them together.
rescope --burp -u bugcrowd.com/bugcrowd -u hackerone.com/security -o importme.jsonGot a whole bunch? Feel free to throw them in a list.
$ cat bigscope.txt
bugcrowd.com/bugcrowd
hackerone.com/security
hackenproof.com/hacken/hackenproof
intigriti.com/intigriti/intigriti
openbugbounty.org/bugbounty/mogiwitt/
yeswehack.com/programs/yes-we-hack And pass it to -i (—-infile) as so.
$ rescope --burp -i bigscope.txt -o bigscope.json --silent
[-] Identified BBaaS program (bugcrowd.com/bugcrowd) in bigscope.txt
[-] Identified BBaaS program (hackerone.com/security) in bigscope.txt
[-] Identified BBaaS program (hackenproof.com/hacken/hackenproof) in bigscope.txt
[-] Identified BBaaS program (intigriti.com/intigriti/intigriti) in bigscope.txt
[-] Identified BBaaS program (openbugbounty.org/bugbounty/mogiwitt/) in bigscope.txt
[-] Identified BBaaS program (yeswehack.com/programs/yes-we-hack) in bigscope.txt
[-] Grabbing targets from bigscope.txt
[-] Grabbing targets from bugcrowd.com/bugcrowd
[-] Grabbing targets from hackerone.com/security
[-] Grabbing targets from hackenproof.com/hacken/hackenproof
[-] Grabbing targets from intigriti.com/intigriti/intigriti
[-] Grabbing targets from openbugbounty.org/bugbounty/mogiwitt
[-] Grabbing targets from yeswehack.com/programs/yes-we-hack
[-] Parsing to JSON (Burp Suite)
[✓] Done. Wrote 193234 bytes to bigscope.jsonPretty neat ye? You can even combine private and public scopes if you want. Again, see repo for details.
Quick install
go get -u github.com/root4loot/rescope
If you run into merge issues from v0.1 then delete the repo and install once again (sorry for the inconvenience.)
Hope you found this useful and if you did then feel free to follow me on Twitter for future updates and other cool things to come. As always, let me know if you run into any issues. Good luck!