A security model is a multilayered framework made of many integrated entities and logical and physical protection mechanisms, all working together to provide a secure system that complies with industry best practices and regulations.
A security policy is a set of rules, practices, and procedures dictating how sensitive information is managed, protected, and distributed. In the network security realm, policies are usually point specific, which means they cover a single area. A security policy is a document that expresses exactly what the security level should be by setting the goals of what the security mechanisms are to accomplish. Security policy is written by higher management and is intended to describe the "whats" of information security. The next section gives a few examples of security policies. Procedures, standards, baselines, and guidelines are the "hows" for implementation of the policy. Information security policies underline the security and well-being of information resources; they are the foundation of information security within an organization.
Trust is one of the main themes in many policies. Some companies do not have policies because they trust in their people and trust that everyone will do the right thing. But, that is not always the case, as we all know. Therefore, most organizations need policies to ensure that everyone complies with the same set of rules.
In my experience, policies tend to elevate people's apprehension because people do not want to be bound by rules and regulations. Instead, people want freedom and non-accountability. A policy should define the level of control users must observe and balance that with productivity goals. An overly strict policy will be hard to implement because compliance will be minimal or ignored. On the contrary, a loosely defined policy can be evaded and does not ensure accountability and responsibility. A good policy has to have the right balance.
Depending on the size of the organization, potentially dozens of security policy topics may be appropriate. For some organizations, one large document covers all facets; at other organizations, several smaller, individually focused documents are needed. The sample list that follows covers some common policies that an organization should consider.
Acceptable use: This policy outlines the acceptable use of computer equipment. The rules are established to protect the employee and the organization. Inappropriate use exposes the company to risks including virus attacks, compromise of network systems and services, and legal issues.
Ethics: This policy emphasizes the employee's and consumer's expectations to be subject to fair business practices. It establishes a culture of openness, trust, and integrity in business practices. This policy can guide business behavior to ensure ethical conduct.
Information sensitivity: This policy is intended to help employees determine what information can be disclosed to nonemployees, as well as the relative sensitivity of information that should not be disclosed outside an organization without proper authorization. The information covered in these guidelines includes but is not limited to information that is either stored or shared via any means. This includes electronic information, information on paper, and information shared orally or visually (such as by telephone, video conferencing, and teleconferencing).
E-mail: This policy covers appropriate use of any e-mail sent from an organization's e-mail address and applies to all employees, vendors, and agents operating on behalf of the company.
Password: The purpose of this policy is to establish a standard for creation of strong passwords, the protection of those passwords, and the frequency of change.
Risk assessment: This policy is used to empower the Information Security (InfoSec) group to perform periodic information security risk assessments (RA) for the purpose of determining areas of vulnerability and to initiate appropriate remediation.
Note
Policies need to be concise, to the point, and easy to read and understand. Most policies listed previously are on average two to three pages.
Standards are industry-recognized best practices, frameworks, and agreed principles of concepts and designs, which are designed to implement, achieve, and maintain the required levels of processes and procedures.
Like security policies, standards are strategic in nature in that they define systems parameters and processes.
Standards vary by industry. There are two notable standards in security information management—ISO 17799 and COBIT. These are discussed in Chapter 25, "Security Framework and Regulatory Compliance."
Procedures are low-level documents providing systematic instructions on how the security policy and the standards are to be implemented in a system. Procedures are detailed in nature to provide maximum information to users so that they can successfully implement and enforce the security policy and apply the standards and guidelines of a security program.
Employees usually refer to procedures more often than other policies and standards because procedures provide the actual details of the implementation phase of a security program.
A baseline is the minimum level of security requirement in a system. Baselines provide users the means to achieve the absolute minimum security required that is consistent across all the systems in the organization. For example, a company might have a baseline for Windows 2000 servers to have Service Pack 4 installed on each server in the production environment. The procedure document would supplement the baseline by spelling out step-by-step instructions on where to download Service Pack 4 and how to install it to comply with this security level.
Guidelines are recommended actions and operational guides for users. Similar to procedures, guidelines are tactical in nature. The major difference between standards and guidelines is that guidelines can be used as reference, whereas standards are mandatory actions in most cases.
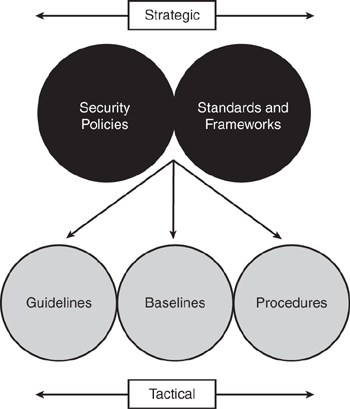
Figure 1-3 depicts the fundamental relationship among security policies, standards, baselines, guidelines, and procedures.