Network security is a continuous process built around the corporate security policy. The security wheel depicted in Figure 1-6 shows a recursive, ongoing process of striving toward perfection—to achieve a secured network infrastructure. The paradigm incorporates the following five steps:
Step 1. | Develop a security policy A strong security policy should be clearly defined, implemented, and documented, yet simple enough that users can easily conduct business within its parameters. |
Step 2. | Make the network secure Secure the network by implementing security solutions (implement authentication, encryption, firewalls, intrusion prevention, and other techniques) to stop or prevent unauthorized access or activities and to protect information and information systems. |
Step 3. | Monitor and respond. This phase detects violations to the security policy. It involves system auditing and real-time intrusion detection and prevention solutions. This also validates the security implementation in Step 2. |
Step 4. | Test. This step validates the effectiveness of the security policy through system auditing and vulnerability scanning and tests existing security safeguards. |
Step 5. | Manage and improve. Use information from the monitor and test phases to make improvements to the security implementation. Adjust the corporate security policy as security vulnerabilities and risks are identified. Manage and improve corporate security policy. |
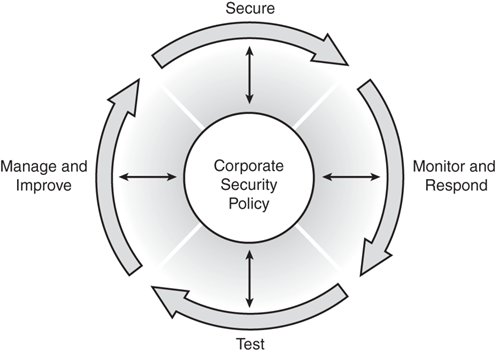
Lessons learned from Steps 2 through 5 should always be reflected back to the corporate security policy in Step 1, so that the high-level security expectations are being met. This should be an ongoing process, a continuous life cycle!