The use of technology continues to expand in this digital age with the ever-increasing volume of data. An exponential amount of data is crossing the networks today. Without any security mechanism in place, each network has complete access to the other with no way of differentiating between authorized and unauthorized activity.
One of the fundamental steps necessary to control network access is the capability to control the data flow within a network. One of the many ways to achieve this is to use an ACL, or access control list (commonly referred to as ACL). ACLs are effective, easy to configure, and available across all major Cisco products.
This chapter focuses primarily on the use and configuration of ACLs available on Cisco IOS and other devices for traffic filtering. The chapter also gives an overview of IP addressing, IP classes, subnets, and masks.
Cisco IOS provides traffic-filtering capabilities for ACLs with the capability to prevent traffic from entering or exiting the network. The use of an ACL is also sometimes referred to as filtering, because it regulates traffic by allowing or denying network access.
An ACL is essentially a list of permit or deny statements that control network access to enforce a security policy. ACLs are an integral part of the end-to-end security solution. Products and technologies such as firewalls, encryption and authentication, and intrusion detection and prevention solutions, however, should be part of an integrated approach to implementing any corporate security policy.
ACLs have many applications (available across all Cisco platforms), including traffic filtering; however, ACLs cannot be used as a replacement or substitute for context-based stateful firewalls, which will be discussed further in Chapter 5, "Cisco IOS Firewall," and Chapter 6, "Cisco Firewalls: Appliance and Module."
ACLs are used in numerous ways. Some common applications of ACLs include the following:
Filtering routing information received from or sent to the adjacent neighbor(s)
Controlling interactive access to prevent unauthorized access to the devices in the network—for example, Console, Telnet, or SSH access
Securing the router by limiting access to services on the router such as Hypertext Transfer Protocol (HTTP), Simple Network Management Protocol (SNMP), and Network Time Protocol (NTP)
Defining interesting traffic for dial-on-demand routing (DDR)
Defining interesting traffic for IPsec virtual private network (VPN) encryption
Several applications in IOS quality of service (QoS) features
Extensive use in security techniques and technologies (for example, TCP Intercept and IOS Firewall)
ACLs can be used to provide a basic level of security for all traffic accessing or traversing the network. If ACLs are not configured, all packets passing through the router would be allowed onto all parts of the network.
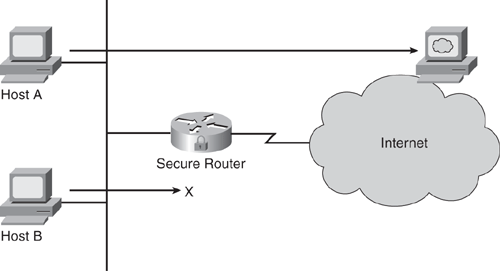
For example, ACLs can allow one host to access the Internet and prevent another host from accessing the Internet, as shown in Figure 2-1. Host A can access resources on the Internet, whereas access for Host B is denied. ACLs can also be used to determine what type of traffic is forwarded or blocked at the router interfaces. For example, all HTTP traffic can be permitted, while FTP traffic is blocked. This is just a simple example; much more complex scenarios can be achieved by using ACLs.
ACLs can be used on a device as the first line of defense for the network. This can be achieved using an ACL on routers, switches, or firewalls that are placed between an internal network (protected zone) and an external network (unprotected zone), such as the Internet. ACLs can also be used on a device placed between two parts of the network, to control traffic entering or exiting a specific part of the network. Another alternative is to use ACLs to filter inbound traffic or outbound traffic on a device, or both for that matter. ACLs should be defined on a per-protocol and per source/destination/port basis to achieve more granularity and control on various types of traffic.
To better understand the use of ACLs, the next sections provide an overview of basic IP addressing, subnets and masks, and IP classes.