This section helps you to understand ACL processing by explaining inbound and outbound ACLs, packet flow rules, and guidelines for implementing ACLs.
Examine the pseudocode that follows to understand packet processing. When an inbound ACL is applied on an interface, the router checks the received packet against the ACL's statements for a match.
if {a match is found} then if {the action is to permit) then {router continues to process the packet} else {the action is to deny} then {router discards the packet sending an ICMP Unreachable message to the source address in the packet - assuming this is not disabled} endif else {a match is not found} then {with the default 'implicit deny' statement—the router discards the packet, sending an ICMP Unreachable message} endif
Examine the pseudocode that follows to understand packet processing. When an outbound ACL is applied on an interface, the router first performs a route lookup for the destination address in the routing table to determine the exit (egress) interface.
if {valid path found in routing table} then if {a match is found} then if {the action is to permit) then {router continues to process the packet} else {the action is to deny} then {router discards the packet sending an ICMP Unreachable message to the source address in the packet - assuming this is not disabled} endif else {a match is not found} then {with the default 'implicit deny' statement—the router discards the packet, sending an ICMP Unreachable message} endif else {valid path not found in routing table, the router drops the packet} endif
Figure 2-3 shows the logical flowchart for how a packet is processed against an inbound or outbound ACL.
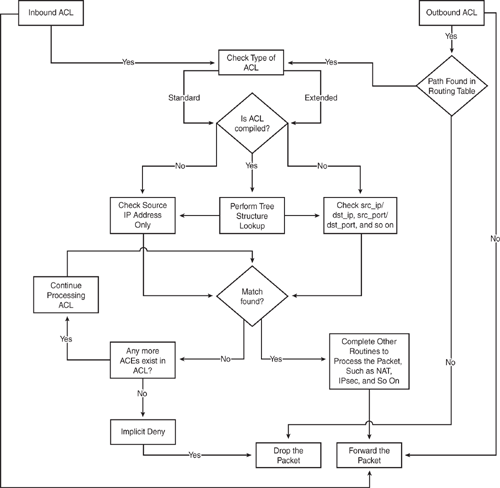
The packet flowchart shown in Figure 2-4 demonstrates how ACL rules are applied to various packet types such as nonfragments, initial fragments, and noninitial fragments that are checked against an ACL.

RFC 1858 covers security considerations for IP fragment filtering and highlights two attacks with two defending mechanisms involving an IP fragment attack.
Note
The noninitial fragment packet contains only Layer 3 information, not Layer 4 information, although the ACL may contain both Layer 3 and Layer 4 information.
Note
Figure 2-4 is taken from the Cisco documentation URL listed here. For more details on ACLS and IP Fragments, visit http://www.cisco.com/warp/public/105/acl_wp.html.
Following are some general guidelines to consider when implementing ACLs: