Securing devices in a network is one of the most important tasks in network security. This chapter describes general principles for protecting the device itself, beginning with a device security policy. In describing these general principles, the chapter focuses on routers, switches, firewalls, concentrators, and intrusion-detection devices. The chapter describes a number of important security tasks, including accessing methods and controls, hardening configuration, identifying unwanted services, managing devices, and monitoring and auditing services. Device-specific features available for administration devices such as firewalls, concentrators, and Intrusion Prevention Systems (IPS) are also discussed. The last part of the chapter presents a basic checklist for device security.
As discussed in Chapter 1, "Overview of Network Security," security policies are of utmost importance. They are a set of rules, practices, and procedures that dictate how sensitive information is managed, protected, and distributed. Among several types of policies, one is developed to establish the rules for protecting devices.
Cisco devices such as routers, switches, firewalls, and concentrators are an integral part of the network, and securing these devices is an essential part of the overall network security policy.
An organization must have a device security policy that dictates the rules to protect device access and access control. The device security policy can also outline the minimal security configuration for all devices in the network they serve.
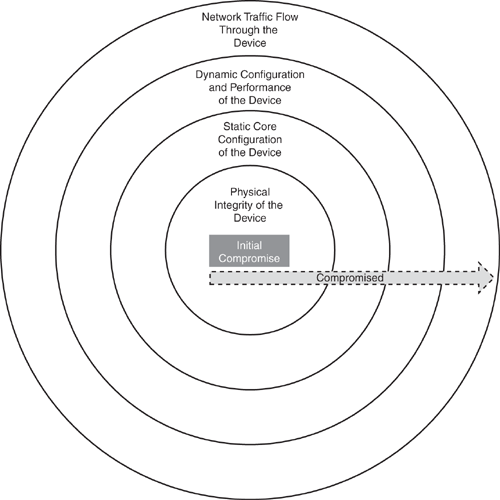
Figure 3-1 shows a conceptual layered view of device security. The security of each layer depends on the security of the layers within. For example, if physical security is compromised (the inner layer), all other layers above will also be affected, resulting in a domino effect.
A device security policy should define rules that spell out who, where, and how these devices will be accessed, in terms of both administrative roles and network services. The device security policy must blend into the overall framework of the high-level requirements of the network security policy.