To configure CBAC, perform the following steps:
Step 1. | Select an interface: internal or external. |
Step 2. | Configure an IP access list. |
Step 3. | Define an inspection rule. |
Step 4. | Configure global timeouts and thresholds (optional). |
Step 5. | Apply the access list and the inspection rule to an interface. |
Step 6. | Verify and monitor CBAC. |
CBAC can be configured either on an internal or external interface of the firewall.
Internal refers to the trusted/protected side where sessions must originate for traffic to be permitted through the firewall.
External refers to the untrusted/unprotected side where sessions cannot originate. Sessions originating from the external side will be blocked.
Although CBAC is recommended to be configured in one direction per interface, it can be configured in two directions (also known as bidirectional CBAC) at one or more interfaces when the networks on both sides of the firewall require protection, such as with extranet or intranet configurations, and for protection against DoS attacks.
For CBAC to work, an IP access list is configured to create temporary openings through the firewall to allow return traffic. It is important to remember that the access list must be an extended access list.
There is no basic template for configuring the access list. Configuration depends on the security policy of an organization. The access list should be kept simple, starting with a basic initial configuration. Making the access list complex and cluttered could unintentionally introduce security risks by allowing unwanted traffic through the firewall, thereby putting the protected network at risk. It is essential to understand and verify the access list before applying it in a production environment.
Follow these general guidelines to create an access list:
Explicitly block all network traffic that originates from the unprotected zone and moves to the protected zone, unless required. For example, when hosting a web server in the protected zone, it is explicitly required to permit HTTP (TCP port 80) that originates from the unprotected zone.
CBAC requires defining an inspection rule to specify which IP traffic (application-layer protocols) will be inspected by the firewall engine.
An inspection rule should specify each desired application-layer protocol as well as the generic TCP or UDP if required. The inspection rule consists of a series of statements, each listing a protocol that specifies the same inspection rule name, as shown in Example 5-5. Inspection rule statements can include other options, such as controlling alert and audit trail messages and checking IP packet fragmentation.
Use the ip inspect name global configuration command to create a CBAC inspection rule set for the required application-layer protocol. Example 5-5 shows how to enable inspection for HTTP, FTP, SMTP, and generic TCP and UDP protocols. Other application protocols (not defined here) can be enabled as required.
Router(config)# ip inspect name myfw http Router(config)# ip inspect name myfw ftp Router(config)# ip inspect name myfw smtp Router(config)# ip inspect name myfw tcp Router(config)# ip inspect name myfw udp |
CBAC uses several timeout and threshold values to determine the state of the session and the duration for which it is maintained. At times, connections are continually maintained for abruptly terminated sessions that occupy unnecessary resources. Incomplete sessions, idle (unused) sessions, or abruptly terminated sessions can be cleared using the timeout and threshold values.
The timeout and threshold values can be used either with default values or can be tuned to suit the network requirement. Table 5-1 shows the available CBAC timeout and threshold commands and their default values. Use the commands listed in the table to modify global timeout or threshold values as required.
For CBAC to take effect, the access list and the inspection rules configured earlier need to be applied to the interface.
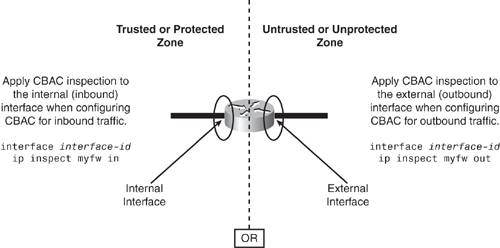
Deciding where CBAC should be configured (internal or external interface) is subjective. As shown in Figure 5-3, CBAC inspection can be configured on either internal or external interfaces—a decision that depends entirely on the security policy. When making that decision, consider which segment is required to be protected:
Apply CBAC inspection to the external (outbound) interface when configuring CBAC for outbound traffic.
Apply CBAC inspection to the internal (inbound) interface when configuring CBAC for inbound traffic.
To apply an inspection rule to an interface, use the ip inspect inspection-name {in | out} command in interface configuration mode.
Use the show ip inspect [config | interface] command or the show ip inspect all command to verify CBAC configuration settings. To view the statistics and session information table with all the established and half-open connections for all session flow through the firewall, use the show ip inspect session [detail] command. In addition, use the show ip access lists command to verify the dynamic access list entries populated in the firewall access list, as shown in Example 5-1 and Example 5-2.
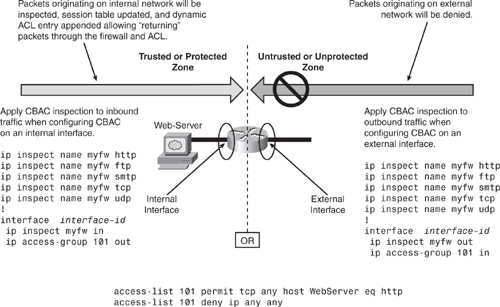
Figure 5-4 depicts a simple CBAC scenario for protecting a web server in the internal network. CBAC inspection can be applied on internal or external interfaces. Access list 101 shows that HTTP traffic that originates from an external network that is external to the web server is permitted. All other traffic is explicitly denied. Traffic originating from the internal network (protected zone) will pass through. Maintaining session table and a corresponding dynamic ACL entry will be punched in ACL 101 to allow all returning traffic.