The new ZFW feature was introduced in Cisco IOS Software Release 12.4(6)T for the enhanced Cisco IOS Firewall feature set.
All features from prior to IOS Software Release 12.4(6)T are inclusive in this new implementation and are supported in the new zone-based inspection.
ZFW supports the following features:
Stateful packet Inspection (SPI)
VRF-aware Cisco IOS Firewall
URL filtering
Denial-of-service (DoS) mitigation
More ZFW features were added into Cisco IOS Software Release 12.4(9)T for per-class session/connection and throughput limits, as well as application inspection and control:
HTTP
Post Office Protocol (POP3)
Internet Mail Access Protocol (IMAP)
Simple Mail Transfer Protocol and Enhanced Simple Mail Transfer Protocol (SMTP/ESMTP)
Sun Remote Procedure Call (RPC)
Instant Messaging (IM) applications, including Microsoft Messenger (MSN), Yahoo Messenger, and AOL Instant Messenger
Peer-to-peer (P2P) file sharing, including Bittorrent, KaZaA, Gnutella, and eDonkey
Note
Stateful inspection for multicast traffic is not supported in ZFW or legacy classic Firewall CBAC.
Before the ZFW was introduced, the Cisco IOS Firewall offered stateful inspection using the CBAC feature. CBAC was covered in detail in the previous sections of this chapter.
In the recent releases of Cisco IOS Software from Version 12.4(6)T and later, the CBAC model is being replaced with the new configuration model that uses ZFW.
This new feature was added mainly to overcome the limitations of the CBAC that was employing stateful inspection policy on an interface-based model. To be specific, the limitation was that all traffic passing through the interface was subject to the same inspection policy, thereby limiting the granularity and policy enforcement, particularly in scenarios where multiple interfaces existed.
With ZFW, stateful inspection can now be applied on a zone-based model. Interfaces are assigned to zones, and policy inspection is applied to traffic moving between zones. This enhancement provides more granularity, flexibility, scalability, and an easy-to-use zone-based security approach. With a zone-based inspection model, varying interzone policies can be applied to multiple hosts or groups of hosts connected to the same interface.
Tip
The following Cisco whitepaper URL provides more details on the conceptual difference between Cisco IOS Classic and ZFW features: www.cisco.com/en/US/products/sw/secursw/ps1018/products_white_paper0900aecd806f31f9.shtml.
Security Zones establish the security boundaries of the network where traffic is subjected to policy restrictions as it crosses to another region within the network.
As shown in Figure 5-7, a zone can have one or more interface(s) assigned to it. This example shows a Cisco IOS Firewall router with four interfaces and three zones:
Interfaces #2 and #3 connected to a Private zone connecting file servers and clients on a LAN (on separate physical interfaces, but in the same security zone), which must not be accessible from the public Internet
Interface #4 connected to the DMZ zone, connecting a web server and Domain Name System (DNS) server, which must be accessible to the public Internet
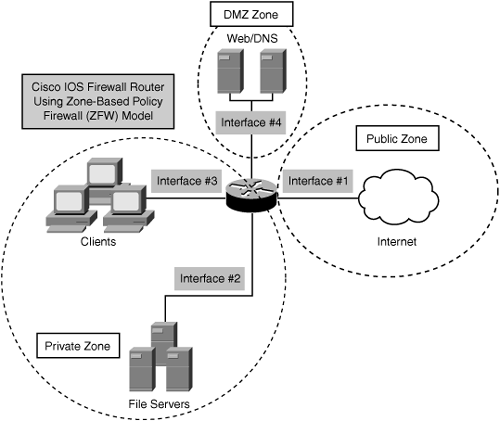
In the example illustrated by Figure 5-7, the IOS Firewall will typically have three main security policies:
Private zone connectivity to DMZ
Public zone connectivity to DMZ
Devices connected in the private zone would be able to pass traffic to all other devices between interface #2 and #3 because they are in the same Private zone. If an additional new interface is added to the Private zone, inter-interface and intra-interface traffic is allowed within the same zone. Additionally, the hosts' traffic to hosts in other zones would be similarly affected by existing policies.
ZFW does not use the classical CBAC ip inspect command set. ZFW policies are configured with the new Cisco Policy Language (CPL), which employs a hierarchical structure to define inspection for network protocols and the groups of hosts to which the inspection will be applied. Note that the two configuration models (Classical CBAC and new ZFW) can be used concurrently on the same router; however, they cannot be combined on the same interface overlapping each other. An interface cannot be configured as a zone member and be configured for ip inspect simultaneously.
Note
It is important to understand that ZFW completely changes the configuration syntax for Cisco IOS Firewall stateful inspection, as compared to Classical CBAC.
ZFW is configured using the new command set of Cisco Policy Language (CPL). CPL is the new format to enable ZFW. The format is similar to the Modular QoS CLI (MQC) in using class-map to identify the traffic and the action applied in a policy map.
Several steps are required to complete the configuration. Although the sequence of tasks that follows is not important, some tasks depend on each other. For example, class-map must be configured before it can be used in the policy-map. Similarly, the policy-map cannot be assigned to a zone-pair before configuring the policy-map itself, and so on.
The following tasks are required to complete the ZFW configuration using the CPL:
Define zones
Define zone-pairs
Define class-map(s) that identify the traffic that must have policy applied as it traverses a zone-pair
Define a policy-map to apply action to the traffic in a class-map
Apply a policy-map to a zone-pair
Assign interface(s) to zones
Note
By default, traffic between the zones is blocked unless an explicit policy dictates the permission.
Based on Figure 5-8, Example 5-7 shows a very basic ZFW configuration that uses the new CPL command set in two zones.
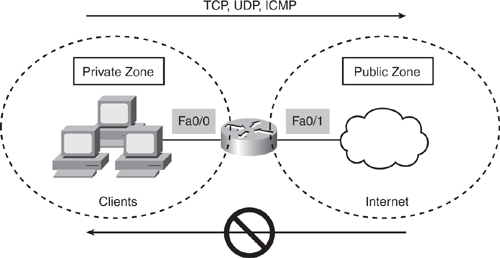
|
Code View: <omit> class-map type inspect match-any myclass match protocol tcp match protocol udp match protocol icmp ! policy-map type inspect mypolicy class type inspect myclass inspect ! zone security private zone security public ! zone-pair security mypair source private destination public service-policy type inspect mypolicy ! Interface FastEthernet0/0 zone-member security private ! interface FastEthernet0/1 zone-member security public ! <omit> |
In addition to the extensive ZFW features and capabilities, ZFW extends the function of application inspection and control (AIC) engine by providing additional capabilities to the ZFW. AIC policies are applied at Layer 7 of the OSI model, performing deep packet inspection at the application-protocol level.
ZFW offers application inspection and control for the following application services:
HTTP
SMTP
POP3
IMAP
Sun remote procedure call
Peer-to-peer application traffic
Instant Messaging applications
Note
AIC is configured as an additional set of application-specific class-maps and policy-maps, which are then applied to existing inspection class-maps and policy-maps.