In addition to the stateful-inspection previously discussed, the Adaptive Security Algorithm is enhanced with powerful capabilities and is built with application-layer intelligence that assists in detecting and preventing protocol and application-layer attacks. It performs deep packet inspection of application-layer protocol traffic (such as HTTP) by checking the packet IP header and the payload contents. Conventional firewalls maintain the session information details up to Layer 4, whereas the Security Appliance adds another tier of security by extending its inspection in the data payload at Layer 7.
With the application-layer awareness, Security Appliance performs deep packet inspection in the data payload for any malicious activity. As shown in Figure 6-4, when the Security Appliance receives a packet that is of well-known application protocol (such as HTTP), it further examines the packet for respective application operation to check for adherence to RFC standards and compliance operations to ensure there is no malicious intent. If the packet is crafted maliciously with unauthorized, nonstandard activity and found to be performing noncompliance operations (illegal commands), the packet is blocked. In a conventional access-list filtering, this packet would be allowed, because only the Layer 3 and Layer 4 information in the packet would be checked.
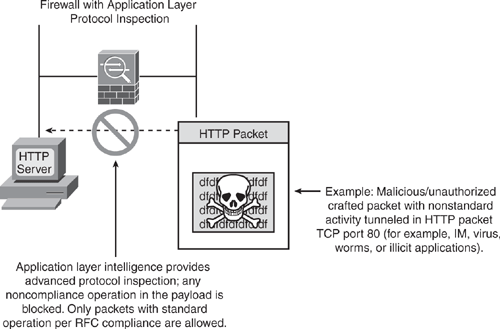
The Security Appliance armed with the application intelligence provides protection from several types of network attacks that use the embedding technique to pass malicious traffic encapsulating in well-known application protocols.
Application inspection is enabled by default for most standard well-known protocols with specific TCP or UDP port numbers. See Table 6-2 for a complete list of supported protocols, with their respective standard compliance enforcement. Security Appliance can be tuned to inform the inspection engine to listen on nonstandard ports. For example, the HTTP port can be changed from a standard TCP/80 to a nonstandard TCP/8080 port. Some protocols cannot be changed; Table 6-2 identifies which protocols can be modified to inspect for nonstandard ports. The Modular Policy Framework Command Line Interface (CLI) is used to change the default settings for application inspection for any application layer inspection (discussed further in this chapter). The MPF is similar to the Cisco IOS Software technique called Modular QoS CLI (MQC).
| Application | PAT? | NAT (1-1)? | Ports Can Be Modified to Nonstandard? | Default Port | Standards Compliance |
|---|---|---|---|---|---|
| CTIQBE | Yes | Yes | Yes | TCP/2748 | — |
| DNS | Yes | Yes | No | UDP/53 | RFC 1123 |
| FTP | Yes | Yes | Yes | TCP/21 | RFC 959 |
| GTP | Yes | Yes | Yes | UDP/3386 UDP/2123 | — |
| H.323 | Yes | Yes | Yes | TCP/1720 UDP/1718 UDP (RAS) 1718-1719 | ITU-T H.323, H.245, H225.0, Q.931, Q.932 |
| HTTP | Yes | Yes | Yes | TCP/80 | RFC 2616 |
| ICMP | Yes | Yes | No | — | — |
| ICMP ERROR | Yes | Yes | No | — | — |
| ILS (LDAP) | Yes | Yes | Yes | — | — |
| MGCP | Yes | Yes | Yes | 2427, 2727 | RFC 2705bis-05 |
| NBDS / UDP | Yes | Yes | No | UDP/138 | — |
| NBNS / UDP | No | No | No | UDP/137 | — |
| NetBIOS over IP3 | No | No | No | — | — |
| PPTP | Yes | Yes | Yes | 1723 | RFC 2637 |
| RSH | Yes | Yes | Yes | TCP/514 | Berkeley UNIX |
| RTSP | No | No | Yes | TCP/554 | RFC 2326, RFC 2327, RFC 1889 |
| SIP | Yes | Yes | Yes | TCP/5060 UDP/5060 | RFC 2543 |
| SKINNY (SCCP) | Yes | Yes | Yes | TCP/2000 | — |
| SMTP/ESMTP | Yes | Yes | Yes | TCP/25 | RFC 821, 1123 |
| SQL*Net | Yes | Yes | Yes | TCP/1521 (v.1) | — |
| Sun RPC | No | Yes | No | UDP/111 TCP/111 | — |
| XDCMP | No | No | No | UDP/177 | — |
| The information in Table 6-2 is taken from "Cisco Security Appliance Command Line Configuration Guide, Version 7.0" at http://www.cisco.com/en/US/docs/security/asa/asa70/configuration/guide/inspect.html#wp1250375. | |||||