IP Routing is one of the basic initialization steps used when configuring the Security Appliance. Routing is the process of deciding the path for each packet that a Security Appliance handles. The routing table contains a list of IP network addresses for which the Security Appliance is intended to provide IP routing services. After the address translation and other routines are completed, a route identifies the interface and the gateway used to forward packets for a specific destination network. Using the destination IP address in the packet header, the routing mechanism decides whether the packet is to be forwarded if a valid route entry is found in the routing table; if not, the packet is discarded.
Note
The routing mechanism should not be used to implement security policy; it should be used merely as a supporting structure designed to forward packets efficiently and reliably.
Security Appliance supports the following four ways to enable IP Routing:
Static and default routes
OSPF
RIP
EIGRP
Tip
Security Appliance supports up to three equal cost routes on the same interface for load balancing.
The simplest option is to use static or default route(s) to forward the packets. A default route forwards all traffic for which no route is found in the routing table to the gateway address. In contrast, a static route forwards traffic for specified destination networks to the next-hop connected device that is specific in the route statement. No route is required for directly connected networks on the Security Appliance.
Static or default routes are required in transparent mode to forward traffic that originates on the Security Appliance destined for nonconnected networks.
As the name implies, a static route provides IP routing information to the Security Appliance without the need of dynamic routing protocol. A static route has a higher precedence over any dynamic routing protocol and is always the best preference to forward traffic to the desired destination. The default administrative distance for a static route is 1, giving it precedence over other routes discovered by dynamic routing protocols, but not directly connected routes. Connected routes always take precedence over static or dynamically discovered routes. In the event of a multiple entries match for a specified destination address, the longest match is preferred. The longest match is the entry with the highest number of 1 bits in its Routing Mask.
Configure static routes using the route command from the global configuration mode to forward traffic for specified nonconnected destination network. One disadvantage of a static route is that route entry will always remain in the routing table, even if the specified gateway becomes unavailable. This is because no mechanism exists for the Security Appliance to determine that the gateway address is not reachable. (This behavior is prevented when using dynamic routing protocol.) If the specified gateway becomes unavailable, static routes need to be manually removed. However, static routes are removed automatically from the routing table if the specified physical interface goes down, and they are reinstated when the interface comes back up.
Software Version 8.0 introduces another unique feature called Static Route Tracking. This feature supports the capability to track the status of the next-hop IP address in the static route. Prior to this feature, there was no inherent mechanism to determine whether the route was up or down, and routes remain in the routing table even if the next-hop gateway becomes unavailable. The only exception was that if the associated interface on the firewall went down, the routes were removed from the routing table.
The static route tracking feature provides the capability to install backup routes dynamically when the primary route fails.
This feature is also useful to define multiple default routes. An example is defining a primary default route to an ISP gateway and a backup default route to a secondary ISP in case the primary ISP becomes unavailable. Static route tracking can also be enabled for static or default routes obtained through Dynamic Host Configuration Protocol (DHCP) or Point-to-Point Protocol over Ethernet (PPPoE).
This feature works by associating a static route with a predefined monitoring target. The Security Appliance monitors the target by using Internet Control Message Protocol (ICMP) echo request packets. In response, if an ICMP echo-reply message is not received within a specified period, the object is considered down, and the associated static route is removed from the routing table. The backup route is installed dynamically and used in place of the removed route.
The Security Appliance can be configured to use one of the following objects as the monitoring target:
ISP gateway address
Next-hop gateway address
Specific server on the target network, such as a AAA server or the web server
Note
For additional details on static route tracking, refer to the following Cisco documentation URL: http://www.cisco.com/en/US/docs/security/asa/asa80/configuration/guide/ip.html#wp1090243.
To avoid the need to use static route entries for every possible destination network, a default route identifies the default gateway address for forwarding packets for destination network(s) not explicitly found in the routing table. Default routes are put to best use in topologies where learning all or more specific networks is not desirable, as in the case of stub networks, or networks with only a single link connecting to the external network (or Internet). A default route is simply a static route (with a destination address/mask pair of 0.0.0.0/0) that is configured using the same route command used to define static routes and is usually aimed toward the external network on the outside interface.
The Security Appliance has the capability to define a separate default route for encrypted traffic along with the standard default route. Use the tunneled option in a default route statement to define a separate gateway address for forwarding all encrypted traffic. The tunneled option does not support multiple equal-cost path routes. Example 6-5 shows a Security Appliance configured with two default routes, one for the non-encrypted traffic and another for encrypted traffic. Non-encrypted traffic for which there is no static or dynamically learned route is forwarded to gateway 209.165.201.1. Encrypted traffic for which there is no static or dynamically learned route is forwarded to gateway 209.165.201.2.
hostname(config)# route outside 0.0.0.0 0.0.0.0 209.165.201.1 hostname(config)# route outside 0.0.0.0 0.0.0.0 209.165.201.2 tunneled |
Figure 6-8 shows an example to configure a static and default route. A default route is configured to send all traffic to the upstream device on the outside interface. Network A and Network B are nonconnected networks; hence, two static routes are created that send traffic destined for Network A (172.16.1.0/24) to the downstream router (10.1.1.2) that is connected to the inside interface, and for Network B (192.168.1.0/24) to the downstream router (10.1.2.2) connected to the DMZ interface.
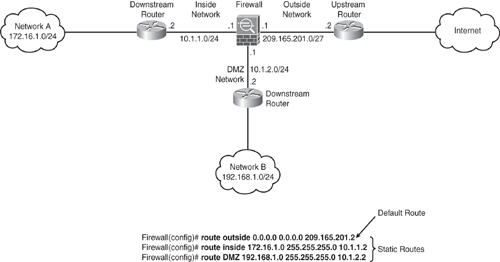
For load balancing, the Security Appliance offers the ECMP that supports up to three equal-cost routes to the same destination per interface. Based on an algorithm that hashes the source and destination IP addresses, the Security Appliance load balances the traffic among the specified gateways. Note that this does not guarantee diverting traffic equally among the gateways.
Example 6-6 shows three equal-cost static routes for destination network 10.1.1.0/24, forwarding traffic to three different gateways on the outside interface.
hostname(config)# route outside 10.1.1.0 255.255.255.0 209.165.201.1 hostname(config)# route outside 10.1.1.0 255.255.255.0 209.165.201.2 hostname(config)# route outside 10.1.1.0 255.255.255.0 209.165.201.3 |
Similarly, up to three equal-cost default routes can be defined per device. Example 6-7 shows three equal-cost default routes, forwarding traffic to three different gateways on the outside interface.
hostname(config)# route outside 0.0.0.0 0.0.0.0 209.165.201.1 hostname(config)# route outside 0.0.0.0 0.0.0.0 209.165.201.2 hostname(config)# route outside 0.0.0.0 0.0.0.0 209.165.201.3 |
Dynamic routing occurs when devices communicate to adjacent devices, informing each other of the reachability of networks. These devices communicate using a routing protocol such as OSPF to exchange route information. Unlike static routing, the routing information populated into the routing tables is added and deleted dynamically by a dynamic routing protocol as routes change over time.
OSPF is an Interior Gateway Protocol (IGP) that distributes routing information among devices. OSPF is used over IP, and OSPF packets are transmitted with an IP data packet with the protocol field in the IP header set to 89. OSPF uses a link-state algorithm to build and calculate the shortest path to all known destinations. The algorithm used to calculate the shortest path is called the Dijkstra algorithm (named after its inventor Edsger W. Dijkstra).
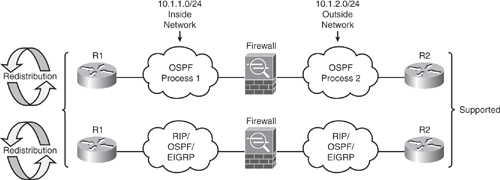
The Security Appliance supports OSPF routing protocol in a manner similar to the IOS. The Security Appliance can run up to two OSPF processes simultaneously, for different sets of interfaces. By default, the two processes will not exchange information unless route redistribution is configured explicitly. The two processes are isolated, as in two separate routing instances in the same device. There are several reasons to have two OSPF processes on the Security Appliance. For example, two processes on the Security Appliance are useful if the Security Appliance has interfaces that use the same IP addresses. (NAT allows these interfaces to coexist, but OSPF does not allow overlapping addresses.) Or, in most cases, a separate OSPF process is enabled on the inside and the outside interfaces (as shown in Figure 6-9), to give you the capability to control route propagation by redistributing a subset of routes between the two processes. Similarly, there could be a requirement to segregate private addresses from public addresses, making two processes necessary.
The cost (also called metric) of an interface in OSPF is inversely proportional to the bandwidth of that interface. A higher bandwidth indicates a lower cost, and a lower-cost path is the preferred route. The formula used to calculate the OSPF cost is
OSPF Cost = 100,000,000 ÷ bandwidth (in bps)
As shown in Figure 6-9, redistribution between the two OSPF processes is supported. Static and connected routes on the Security Appliance can also be redistributed into the OSPF process, but they must be configured on OSPF-enabled interfaces.
As per the Figure 6-9 network diagram, OSPF can be configured on the inside and outside interfaces.
Note
RIP and OSPF on the same firewall appliance was not supported in version 7.0 or prior. However, multiprotocol is now fully supported from v7.2 and later, as illustrated in Figure 6-9.
Example 6-8 shows how to enable two separate OSPF processes with mutual two-way redistribution to allow devices on both sides of the Security Appliance to learn networks from each other.
hostname(config)# router ospf 1 hostname(config-router)# network 10.1.1.0 255.255.255.0 area 0 hostname(config-router)# redistribute ospf 2 metric 1 subnets hostname(config)# router ospf 2 hostname(config-router)# network 10.1.2.0 255.255.255.0 area 0 hostname(config-router)# redistribute ospf 1 metric 1 subnets |
Several interface-specific OSPF parameters can be configured as deemed necessary, including OSPF Hello or dead intervals, OSPF priority, and authentication keys. Example 6-9 shows some of the OSPF parameters that can be enabled under the interface.
hostname(config-router)# interface inside hostname(config-interface)# ospf cost 10 hostname(config-interface)# ospf retransmit-interval 10 hostname(config-interface)# ospf transmit-delay 5 hostname(config-interface)# ospf priority 255 hostname(config-interface)# ospf hello-interval 5 hostname(config-interface)# ospf dead-interval 20 hostname(config-interface)# ospf authentication-key cisco hostname(config-interface)# ospf message-digest-key 1 md5 cisco hostname(config-interface)# ospf authentication message-digest |
Several OSPF parameters can be configured under the area that will affect the entire OSPF domain/area. Examples include authentication, route summarization, route filtering, and defining stub areas. Example 6-10 shows some of the OSPF parameters that can be enabled areawide.
hostname(config)# router ospf 1 hostname(config-router)# area 1 default-cost 10 hostname(config-router)# area 1 stub hostname(config-router)# area 1 stub no-summary hostname(config-router)# area 0 range 10.1.1.0 255.255.255.0 hostname(config-router)# area 0 filter-list prefix mylist in |
Securing OSPF networks will provide protection not only from malicious attacks, but also accidental misconfigurations. The receptive nature of OSPF dictates that any router with coordinated configuration parameters (network mask, hello interval, dead interval, and the like) can participate in a given OSPF network. Because of this default behavior, any number of accidental factors (misconfigurations, lab machines, test setups, and so on) have the potential to adversely affect routing in an OSPF environment. Authentication provides password-based protection against unauthorized access to an area. The Security Appliance supports OSPF authentication to secure route exchange between the devices. OSPF supports two types of authentication: simple password (clear-text) and MD5 authentication mechanism. Security Appliance supports both.
Example 6-11 shows how to configure areawide OSPF authentication on the Security Appliance.
hostname(config)# router ospf 1 ! Enabling area-wide Simple (clear-text) authentication hostname(config-router)# area 0 authentication ! Enabling area-wide MD5 authentication hostname(config-router)# area 0 authentication message-digest ! Configure OSPF key on the interface hostname(config-router)# interface inside ! Configuring Simple password authentication key hostname(config-interface)# ospf authentication-key cisco ! Configuring MD5 authentication key hostname(config-interface)# ospf message-digest-key 1 md5 cisco |
Alternatively, authentication can be enabled specifically on a link basis (per-interface) and not areawide. This means that both sides of the link on the connected devices must be configured similarly. Example 6-12 shows how to configure interface-based OSPF authentication on the Security Appliance.
hostname(config-router)# interface inside ! Configuring Simple password authentication and key hostname(config-interface)# ospf authentication hostname(config-interface)# ospf authentication-key cisco ! Configuring MD5 authentication and key hostname(config-interface)# ospf authentication message-digest hostname(config-interface)# ospf message-digest-key 1 md5 cisco |
Several useful show commands are available for displaying general information and other OSPF-related information, such as neighbor adjacency status, interface parameters, virtual-link status, and border-routers. The following list includes some of the common OSPF show commands used:
show ospf [process-id [area-id]]: Displays general information about OSPF routing processes.
show ospf interface [if_name]: Displays OSPF-related interface information.
show ospf neighbor [interface-name] [neighbor-id] [detail]: Displays OSPF neighbor adjacency information on a per-interface basis.
show ospf [process-id] virtual-links: Displays OSPF-related virtual links information.
show ospf border-routers: Displays the internal OSPF routing table entries to the Area Border Router (ABR) and Autonomous System Boundary Router (ASBR).
show ospf [process-id [area-id]] database: Displays lists of information related to the OSPF database for a specific device.
show ospf [process-id] summary-address: Displays a list of all summary address redistribution information configured under an OSPF process.
The Routing Information Protocol, or RIP as it is more commonly called, is one of the most enduring of all routing protocols. RIP was defined in RFC 1058 and Internet Standard (STD) 56. Later, the IETF (Internet Engineering Task Force) updated RIP with the release of a revised RFC 1388 in January 1993. RFC 1388 was then superseded in November 1994 by RFC 1723, which describes RIPv2 (the second version of RIP). These RFCs did not attempt to make obsolete the previous version of RIP, but proposed extensions and enhancements to the RIP capabilities. RIPv2 enabled RIP messages to carry more information and scale further with more features, such as multicast support and a next-hop router address. The next-hop router address is an authentication mechanism; its most important function is to support subnet masks and is therefore a critical feature that was not available in RIPv1. RIP is a dynamic, distance-vector routing protocol that uses UDP as the transport protocol. RIP packets are transmitted on UDP port 520 for route updates.
The Security Appliance supports both RIPv1 and RIPv2 protocols. Using RIP has advantages over using static routes, because the initial configuration for RIP is simple and does not require updating the configuration when the topology changes. The downside to RIP (or any other dynamic protocol) is that there is more network and processing overhead than with static routing.
By default, the Security Appliance sends RIPv1 updates and accepts RIPv1 and RIPv2 updates. Redistribution of routes from other routing processes into the RIP is supported in Firewall OS Version 7.2 and later. Prior to this, RIP and OSPF were not supported on the same device.
Unlike IOS, RIP is enabled differently on the Security Appliance. To enable RIP on the Security Appliance for an interface, use the rip command from the global configuration mode. There is no router rip command on the Security Appliance. Both RIP modes (passive and default) can be enabled on an interface by using the rip command.
Example 6-13 shows how to configure passive RIP with simple password authentication and MD5 authentication on inside and outside interfaces. Example 6-13 also shows how to propagate a default route on the inside interface, indicating that the Security Appliance will be the default gateway for the downstream devices. A default route is seldom (in most cases never) advertised out on the outside interface, because in typical network designs, the Security Appliance is not the default gateway for the upstream device.
! Enabling RIPv2 with Simple Password Authentication hostname(config)# rip outside passive version 2 authentication text cisco 1 hostname(config)# rip inside passive version 2 authentication text cisco 1 hostname(config)# rip inside default version 2 authentication text cisco 1 ! Enabling RIPv2 with MD5 Authentication hostname(config)# rip outside passive version 2 authentication md5 cisco 1 hostname(config)# rip inside passive version 2 authentication md5 cisco 1 hostname(config)# rip inside default version 2 authentication md5 cisco 1 |
The Security Appliance OS Software Version 8.0 debuts the support of the Enhanced Interior Gateway Routing Protocol (EIGRP). EIGRP is a Cisco proprietary routing protocol and is available on Cisco devices only. EIGRP on Security Appliance is supported in single mode only; it is not supported in multicontext mode.
The Security Appliance can be configured as an EIGRP stub router, which helps enhance the performance by decreasing memory and processing requirements on the Security Appliance. A firewall configured as an EIGRP stub does not require maintaining a complete EIGRP routing table, because it forwards all nonlocal traffic to a distribution router. The distribution router sends a default route to the stub router/firewall. In some occasions, only specific routes are advertised from the stub router to the distribution router. When the Security Appliance is configured as a stub router, it sends a peer information packet to all neighboring routers to report its status as a stub router. Neighbors receiving this packet will not query the stub for routes. The stub depends on the distribution router to send the proper updates to all peers.
The Security Appliance can be enabled as an EIGRP stub router through the following steps:
Step 1. | Enable the EIGRP routing process from the global configuration mode as follows. The as-num is the Autonomous System number of the EIGRP routing process: firewall(config)# router eigrp as-num |
Step 2. | Configure the interface connected to the distribution router to participate in the EIGRP process: firewall(config-router)# network ip-addr [mask] |
Step 3. | Configure the Security Appliance for the stub routing process. Specific networks must be explicitly defined that need to be advertised by the stub routing process to the distribution router. By default, static and connected networks are not automatically redistributed into the stub routing process. firewall (config-router)# eigrp stub {receive-only | [connected] [redistributed] [static] [summary]} |
By default, EIGRP hello packets are sent as multicast packets. In a nonbroadcast environment such as a tunnel, EIGRP neighbors must be manually defined to send hello packets as unicast messages. To define a static neighbor in EIGRP, use the following command from the router configuration mode:
firewall(config-router)# neighbor ip-addr interface if_name
Multiple static neighbors can be defined using the previously outlined process.
Similar to EIGRP support in a Cisco IOS router, several other optional parameters can be configured on Security Appliance, such as the distribute-list, passive-interface and default-information commands.
EIGRP supports route authentication by using MD5 authentication for all routing updates. The MD5 authentication prevents the introduction of unauthorized or false routing messages from unapproved sources.
Note
EIGRP route authentication is configured on a per-interface basis. All neighbors must be configured with the same authentication mode and key for EIGRP adjacencies to be established.
EIGRP authentication can be enabled on the physical interface as follows:
Step 1. | Enter the physical interface configuration mode for which EIGRP authentication needs to be configured: firewall(config)# interface phy_if |
Step 2. | Enable per-interface MD5 authentication as follows: firewall(config-if)# authentication mode eigrp as-num md5 |
Step 3. | Configure the secure key used by the MD5 algorithm. The key argument can contain up to 16 characters. The key-id argument is a numeric number from 0 to 255: firewall(config-if)# authentication key eigrp as-num key key-id key-id |