NAT, also referred to as IP address masquerading, performs the translation of an IP address that is used within one network (internal network) to a different IP address known within another network (outside world). NAT technology is typically used to hide the IP addresses in an internal network (using RFC 1918 private addressing). The masquerading technique can be seen as a form of security hiding the real identity of the network.
A NAT device performs the following two processes:
Undoing translation for returning traffic.
Firewall Stateful inspection tracks all connections traversing through the Security Appliance by maintaining a translation table and using this table to verify the destination of an inbound packet that matches the source of a previous outbound request.
The firewall has always been a device supporting and even requiring NAT for maximum flexibility and security. NAT control is available as a capability in the new software release on the Security Appliance.
NAT control dictates the firewall if the address translation rules are required for outside communications and ensures that the address translation behavior is the same as versions earlier than 7.0.
The NAT control feature works as follows:
When NAT control is disabled, and the firewall forwards all packets from a higher-security (such as Inside) interface to a lower-security (such as Outside) interface without the configuration of a NAT rule. Traffic from a lower-security interface to a higher-security interface only requires that it be permitted in the access lists, and no NAT rule is required in this mode.
When NAT control is enabled, this dictates the requirement of using NAT. (The NAT rule is compulsory in this case.) When NAT control is enabled, it is also required that packets initiated from a higher security-level interface (such as Inside) to a lower security-level interface (such as Outside) must match a NAT rule (nat command with a corresponding global, or a static command), or else processing for the packet stops. Traffic from a lower-security interface to a higher-security interface also requires a NAT and is permitted in the access lists to be forwarded through the firewall.
The default configuration is the specification of the no nat-control command (NAT control disabled mode). With version 7.0 and later, this behavior can be changed as required.
To enable NAT control, use the nat-control command in the global configuration mode, as shown next:
hostname(config)# nat-controlNote
The nat-control command is available in routed firewall mode and in single and multiple security context modes.
When the nat-control is enabled, each Inside address must have a corresponding Inside NAT rule. Similarly, if an Outside dynamic NAT is enabled on an interface, each Outside address must have a corresponding Outside NAT rule before communication is allowed through the Security Appliance.
By default, NAT control is disabled (no nat-control command). The no nat-control command allows Inside hosts to communicate with outside networks without the need to configure a NAT rule. In essence, with NAT control disabled, the Security Appliance does not perform an address translation function to any packets. To disable NAT control globally, use the no nat-control command in global configuration mode:
hostname(config)# no nat-controlThe difference between the no nat-control command and the nat 0 (identity NAT) command is that identity NAT requires that traffic be initiated from the higher-level interface. The no nat-control command does not have this requirement, nor does it require a static command to allow communication from the lower-level interface (from Outside to Inside); it relies only on access-policies—for example, permitting the traffic in ACL and having corresponding route entries.
To summarize, traffic traversing from a
More Secure to a Less Secure interface
Is designated as outbound traffic.
The firewall will allow all IP-based traffic unless restricted by access lists, authentication, or authorization.
One or more of the following commands are required:
- nat, nat 0, global, static
Less Secure to a More Secure interface
Outside to Inside connections.
Inbound permission is required.
The firewall will drop all packets unless specifically allowed in the access-list that is applied on the arriving interface. Further restrictions apply if authentication and authorization are used.
One or more of the following commands are required:
- nat 0 with ACL, static and inbound access-list on the ingress interface.
Several types of NAT are available. The Security Appliance can be configured to perform any of the following types:
Dynamic NAT
Dynamic Port Address Translation (PAT)
Static NAT
Static PAT
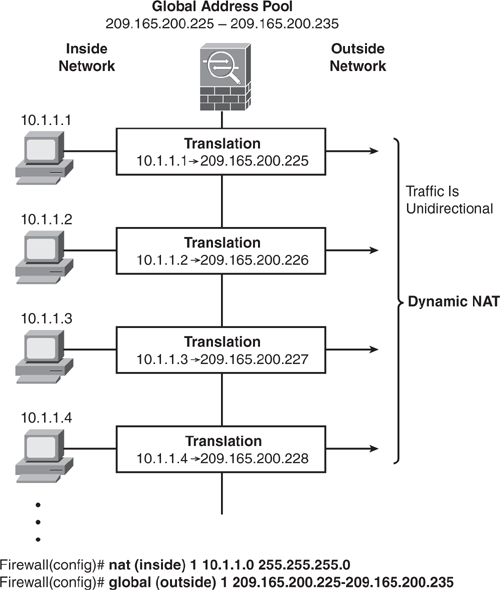
Dynamic NAT translates a group of real (private) addresses to public IP addresses drawn from a pool of registered (public) addresses that are routable on the destination network. When a host initiates a connection to a particular destination, the Security Appliance translates the host source address to the corresponding NAT rule from the mapped pool. The translation is maintained and is valid for the duration of the connection and cleared when the session is terminated. If the same host initiates another connection, there is no guarantee it will acquire the same address from the mapped pool. Addresses from the pool are handed out on a first-come, first-served basis. Therefore, because the translated address varies, the destination-side user cannot initiate inbound connections when dynamic NAT is used. Dynamic NAT and PAT are used for unidirectional communication only. Figure 6-10 shows how dynamic NAT works.
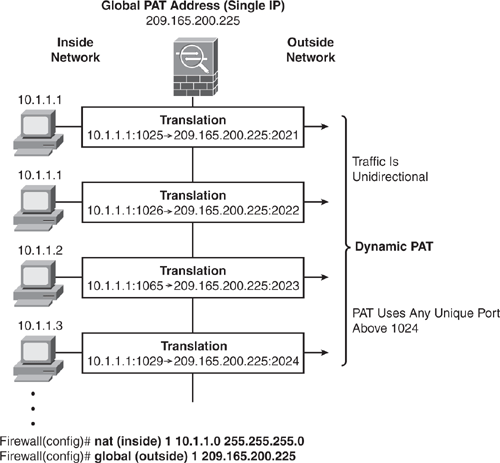
Dynamic PAT translates a group of real (private) addresses that are mapped to a single mapped IP address by using a combination of a mapped IP address and a source port number to create a unique session. Hence, the same IP address is used for all packets with a different source port for each session. The Security Appliance translates the source address and source port (Layer 3 and Layer 4 combination) to the mapped address and a unique port above 1024.
Each connection entails a separate translation because the source port differs for each connection. The translation is maintained and remains valid for the duration of the connection. The translation is cleared when the session is terminated. The port translation also expires after 30 seconds of inactivity. (This timeout is not configurable.) PAT lets you use a single mapped address, thus conserving routable addresses. The interface IP address of the Security Appliance can also be used as the PAT address. Similar to Dynamic NAT, the destination-side user cannot initiate an inbound connection when using dynamic PAT. Figure 6-11 shows how dynamic PAT works.
Note
PAT does not work for some multimedia applications that have a data stream different from the control path.
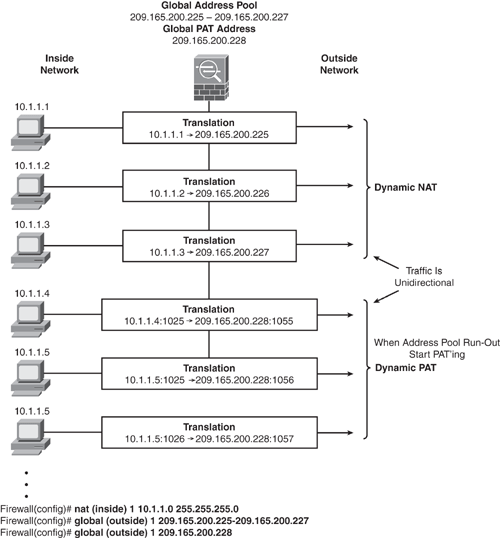
Dynamic NAT and PAT can be enabled concurrently. The Security Appliance first uses all the addresses from the global address pool. When no addresses are available in the global pool, it applies the PAT translation, as shown in Figure 6-12.
To configure dynamic NAT and PAT, perform the following steps:
Step 1. | Identify the real (private) addresses on a given interface that requires translation by using the nat command. |
Step 2. | Configure a corresponding global command to specify the mapped addresses pool for the egress interface. (In the case of PAT, this is one address.) |
Each nat command matches a global command by matching the corresponding NAT ID, a number that is assigned in each command. NAT ID ties the nat and the global commands together. Refer back to Figure 6-10 and Figure 6-11 for demonstration examples.
When using multiple interfaces, the NAT ID can be used to tie multiple NAT rules together. For example, NAT ID 1 can be used to configure nat for Inside and DMZ interfaces. The same ID 1 can then be used to configure the global command on the outside interface. Traffic from the inside interface and the DMZ interface share a mapped pool or a PAT address when exiting the outside interface. Example 6-14 illustrates this scenario.
hostname(config)# nat (inside) 1 10.1.1.0 255.255.255.0 hostname(config)# nat (dmz) 1 10.2.2.0 255.255.255.0 hostname(config)# global (outside) 1 209.165.201.3-209.165.201.10 |
The NAT ID can also be used to reference multiple global commands for exiting interfaces. For example, NAT ID 1 can be used for the global command on Outside and DMZ interfaces, and the same ID can be used for the Inside nat command to identify the traffic to be translated when going to both Outside and DMZ interfaces. Similarly, NAT ID 1 can be used on the DMZ interface, and the global command on the outside interface is also used for DMZ traffic.
hostname(config)# nat (inside) 1 10.1.1.0 255.255.255.0 hostname(config)# nat (dmz) 1 10.2.2.0 255.255.255.0 hostname(config)# global (outside) 1 209.165.201.1-209.165.201.253 hostname(config)# global (outside) 1 209.165.201.254 hostname(config)# global (dmz) 1 10.2.2.254 |
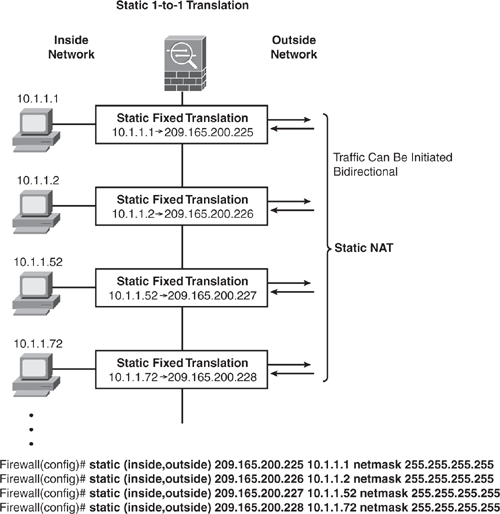
Static NAT creates a fixed translation (one-to-one) of real (private) addresses to mapped (public) addresses. A persistent translation rule exists (mapped address is the same) for each consecutive connection with static NAT. Because the mapped address is always the same, it allows the destination-side network to initiate traffic to a translated host. The static command is used to permanently associate a host address (or entire subnet) on a higher security-level interface with a host address on a lower-security level interface. Static NAT and PAT can be used for bidirectional communication. Figure 6-13 shows an example.
There are several ways to configure address translation. The following examples illustrate a few scenarios.
Example 6-16 shows how to configure static NAT (persistent translation) for an Inside IP address (10.1.1.1) to an Outside IP address (209.165.200.1).
hostname(config)# static (inside,outside) 209.165.200.1 10.1.1.1 netmask 255.255.255.255 |
Example 6-17 shows how to configure an Outside NAT (persistent translation) using a static map for the Outside address (209.165.201.15) to an Inside address (10.1.1.6).
hostname(config)# static (outside,inside) 10.1.1.6 209.165.201.15 netmask 255.255.255.255 |
Example 6-18 shows how to configure a static map (persistent translation) for an entire subnet (1-to-1, host-to-host) with a 24-bit subnet mask.
hostname(config)# static (inside,outside) 209.165.201.0 10.1.1.0 netmask 255.255.255.0 |
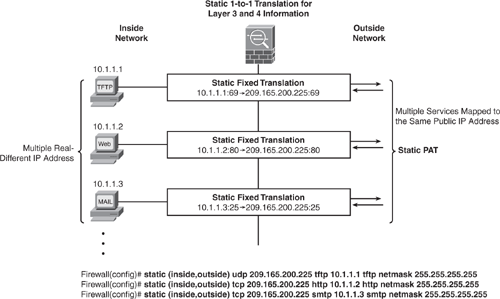
Static PAT is similar to static NAT, with the exception that it allows for specifying the Layer 4 (TCP or UDP) port information for the real and mapped addresses.
This feature is useful for providing a single address for global users to access TFTP, HTTP, and Simple Mail Transfer Protocol (SMTP) services where the services are actually available on different servers on the local network. Define multiple static PAT statements for each server that uses the same mapped (public) IP address with ports mapped to different real IP addresses:
real_ip_A / public_ip_A / TFTP
real_ip_B / public_ip_A / HTTP
real_ip_C / public_ip_A / SMTP
Figure 6-14 shows how to configure static PAT statements for multiple services mapped to the same public IP address.
As discussed earlier, when NAT control is enabled, each connection initiated requires a corresponding NAT rule. One of the following three methods can be used to bypass address translation for specific hosts or networks when NAT control is enabled:
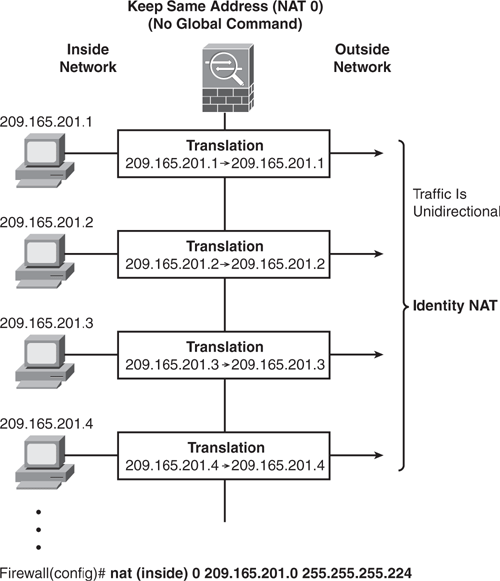
Identity NAT is similar to Dynamic NAT, but it translates the real IP address to the same mapped IP address so that no need exists for a mapped global pool. Only "translated" hosts can create NAT translations, and return traffic is allowed back. Identity NAT can be used only for unidirectional communication. Even though the mapped address is the same as the real address, a connection cannot be initiated from the Outside to the Inside.
Figure 6-15 shows how to configure Identity NAT. The NAT engine will not perform address translation for the inside hosts on the 209.165.201.0/27 network, and the source address remains the same when it exits. This method can also be used when the internal network uses a public routable address and does not require address translation.
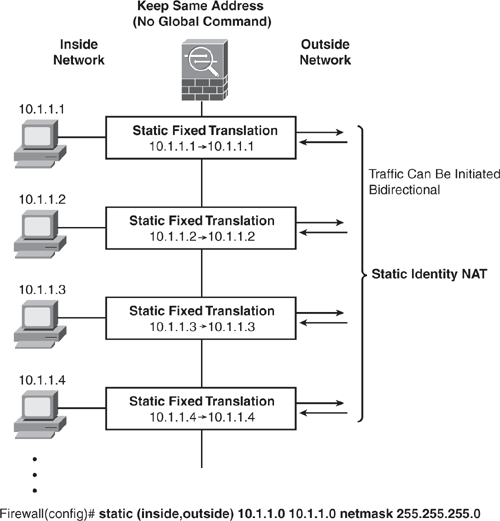
Static identity NAT is similar to static NAT, but it creates a fixed translation (1-to-1) of real addresses while keeping the same mapped addresses. Static identity NAT can be used for bidirectional communication.
Figure 6-16 shows how to configure Static Identity NAT. The NAT engine will not perform address translation for the inside hosts on the 10.1.1.0/24 network, and the source address remains the same when it exits. Outside users can initiate an inbound connection to this address as long as the address is routable on the destination side network.
Example 6-19 shows how to configure Outside Static Identity NAT. The NAT engine will not perform address translation for the Outside host 209.165.201.15 when accessed from Inside.
|
Code View: hostname(config)# static (outside,inside) 209.165.201.15 209.165.201.15 netmask 255.255.255.255 |
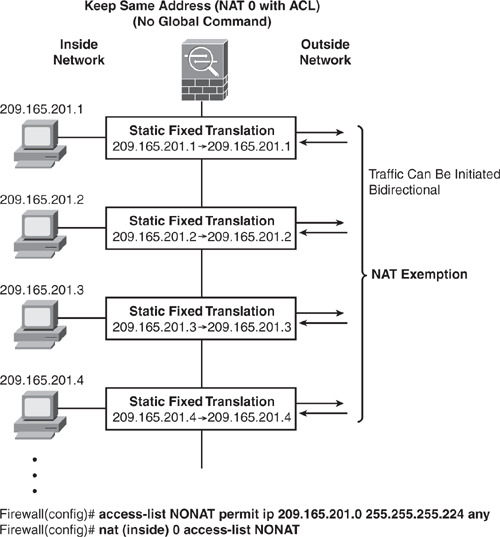
NAT Exemption (nat 0 access-list) is similar to Identity NAT. The main differentiator is that NAT Exemption allows bidirectional communication. NAT Exemption allows both translated and remote hosts to initiate connections.
Figure 6-17 shows how to configure NAT Exemption. The NAT engine will not perform address translation for the inside hosts in 209.165.201.0/27 network, and they will remain the same because they exit out to another interface. Users on the Outside network (destination-side) are also able to initiate connection to a host in the 209.165.201.0/27 network.
Policy NAT is similar to static NAT. However, it allows for defining a conditional criterion to check the source address and the destination address to determine address translation. With this feature, a source address translation can vary, subject to a different destination. For example:
Host A communicating to Server A  translate to Public_IP_A
translate to Public_IP_A
Host A communicating to Server B  translate to Public_IP_B
translate to Public_IP_B
Policy NAT allows identification of local traffic for address translation by specifying the combination of source and destination addresses (or ports) by using an access list. Regular NAT uses source addresses/ports only, whereas policy NAT uses both source and a combination of destination addresses/ports to identify the real address for translation.
Figure 6-18 shows how to configure Policy NAT Exemption by using the nat/global command. The source and destination address pair is checked, and address translation is performed accordingly. In this example, when internal hosts in network 10.1.1.0/24 initiate a connection to any host in network 172.16.1.0/24, the source address will be translated to 209.165.202.1-10.
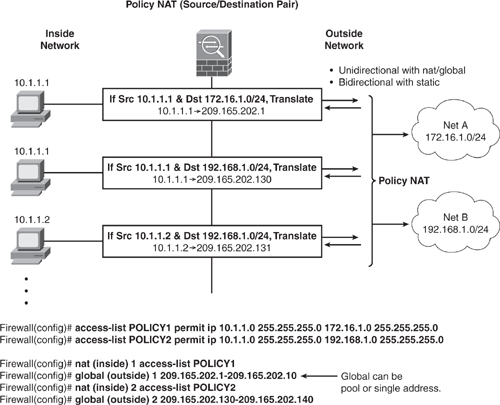
When the same internal hosts in the network 10.1.1.0/24 initiate a connection to any host in network 192.168.1.0/24, the source address will be translated to 209.165.202.130-140 instead. Traffic flow is unidirectional when using the nat/global command, and bidirectional when using the static command.
When several address translation types are configured on the firewall, there is a potential of overlap. The firewall matches real (private) addresses to corresponding NAT rules in the following order of NAT rules processing, until the first match is found.