As discussed in the previous chapter, with networks growing beyond the campus, network security increases in importance and administrative complexity. Identity security and access management are essential for networks and network resources to safeguard them from unauthorized access.
Cisco Secure Access Control Server (ACS) provides a centralized access management solution for managing enterprise-wide network users and network infrastructure resources with policy-based enforcement. ACS provides a comprehensive identity-based network access control solution for intelligent information networks.
Cisco Secure ACS software for Windows provides a scalable, centralized identity-based access control solution. ACS provides the structure to enforce user-based policies and allows granular control of user access to network and network resources.
ACS software supplies the following provisions:
Network access user authentication
Resource authorization and privilege levels
Network access security policy enforcement
Audit information
Access and command controls
Support for RADIUS and TACACS+ security protocols
Cisco Secure ACS is one of the key components in the integration of the Cisco trust and identity security solutions. It provides the structure for access control security by provisioning the authentication, authorization, and accounting (AAA) architecture and policy control from a centralized identity networking framework, thereby allowing greater scalability and flexibility, increased security, and user productivity gains.
ACS support spans all major Cisco devices and other network access servers (NAS), also referred to as AAA client, including
Wired and wireless LAN
Access points
Edge and core routers
Dialup and broadband connections
Cable access solutions
Storage devices
Content devices
Voice over IP (VoIP)
Firewalls
Virtual private networks (VPN)
IEEE 802.1X access control
Cisco Network Admission Control (NAC)
Figure 9-1 depicts the AAA client-server model. Note that the diagram shows the external database as optional. ACS supports local user databases and external databases, which will be discussed further in this chapter.
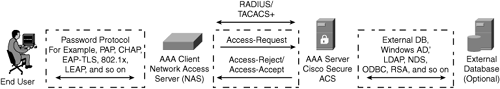
The AAA framework implementation consists of two parts: the client side and the server side. As shown in Figure 9-1, Cisco Secure ACS serves as the AAA server side by providing authentication, authorization, and accounting services to network devices on the AAA client side. The Cisco ACS is also referred to as the network access server (NAS) or network access device (NAD). The NAS/NAD can be any Cisco device, such as the router, switch, firewall, concentrator, access point, or any other non-Cisco device. The AAA client serves as the gateway and forwards all access requests to the AAA server on behalf of the end user. The AAA server verifies the credentials by using its internal local database or optionally configured external database. The AAA server responds to the NAS with an [access-accept] or an [access-reject] message with a set of authorization attributes. Refer back to Figure 9-1 to see the basic flow.
ACS operates as a set of Windows services and can run on Microsoft Windows 2000 Server and the Windows Server 2003 operating system. ACS can be installed as a domain controller or a member server.
For further details, refer to the ACS installation and user guide:
Cisco ACS for Windows Installation Guide: http://www.cisco.com/en/US/products/sw/secursw/ps2086/prod_installation_guides_list.html
Cisco ACS for Windows User Guide: http://tinyurl.com/yvajyj
ACS supports both RADIUS and TACACS+ AAA security protocols.
ACS conforms to TACACS+ protocol as defined by Cisco Systems in draft 1.78 on TCP port 49.
ACS conforms to RADIUS protocol in the following RFCs:
RFC 2138
RFC 2139
RFC 2284
RFC 2865
RFC 2866
RFC 2867
RFC 2868
RFC 2869
The RADIUS ports used in AAA have changed in RFCs. ACS supports both the older and newer RFC-defined ports in its implementation. For authentication and authorization, ACS accepts requests on UDP port 1645 and UDP port 1812. For accounting, ACS accepts requests on both UDP port 1646 and UDP port 1813.
In addition to the AAA protocol support, ACS extends support to the following common password protocols for end-user authentication (see Figure 9-1):
ASCII
Password Authentication Protocol (PAP)
Challenge Handshake Authentication Protocol (CHAP)
AppleTalk Remote Access Protocol (ARAP)
MS-CHAP v1
MS-CHAP v2
Lightweight Extensible Authentication Protocol (LEAP)
Extensible Authentication Protocol Message Digest 5 (EAP-MD5)
Extensible Authentication Protocol Transport Layer Security (EAP-TLS)
Protected Extensible Authentication Protocol (PEAP)
The implementation of the previously mentioned password protocol depends on the support of external databases available in ACS. Table 9-1 lists the Protocol-Database Compatibility reference supported by the various databases.