Cisco Secure ACS server supports the use of token servers to provide a strong security authentication mechanism using the OTP technology.
Cisco Secure ACS provides support for ASCII, Password Authentication Protocol (PAP), and Protected Extensible Authentication Protocol (PEAP)/Extensible Authentication Protocol Generic Token Card (EAP-GTC) authentication by using token servers. No other authentication protocols are supported with token server databases.
Note
For more information about authentication protocols and the Cisco Secure ACS external database types that support token servers, refer to the Authentication Protocol-Database Compatibility: http://tinyurl.com/2fb4nq.
Cisco Secure ACS supports two types of token server implementations:
RADIUS token server: Support for token servers that provide a standard RADIUS interface built in to the token server. This feature enables Cisco Secure ACS to support a RADIUS token server database using any token server that provides an Internet Engineering Task Force (IETF) RFC 2865-compliant RADIUS interface.
Non-RADIUS token server: Support for RSA SecurID token servers only. RSA SecurID does not support the RADIUS interface. ACS uses RSA proprietary client software to talk to the token server. ACS supports Point-to-Point Protocol (PPP); that is, ISDN and Async, and Telnet, for RSA SecurID token servers by acting as a token-client to the RSA SecurID token server. RSA-provided application programming interface (API) client software is installed on the computer that is running Cisco Secure ACS to communicate authentication requests with RSA token server.
Cisco Secure ACS acts as a client to the token server using the RADIUS-enabled interface of the token server, except in the case of RSA SecurID implementation. For RSA SecurID, Cisco Secure ACS uses RSA proprietary API client software.
When Cisco Secure ACS receives an authentication request from the AAA client (NAS), ACS forwards the authentication request to the token server. This process assumes that ACS is configured to authenticate against a token server, as configured in the external database configuration for "unknown user policy."
Figure 10-2 shows a menu option for the Cisco Secure ACS external database configuration, in which both RADIUS-enabled and non-RADIUS (RSA SecurID) token servers can be configured.
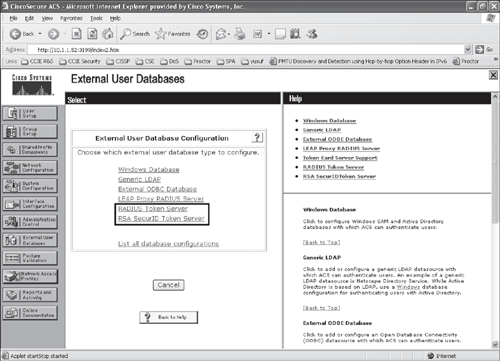
Before configuring the Cisco Secure ACS, it is important that the RADIUS-enabled token server and/or the RSA SecurID token server are installed and configured. In the case of RSA SecurID, ensure that the applicable RSA SecurID API client software is installed on the Cisco Secure ACS server.
Perform the following steps to configure Cisco Secure ACS for a RADIUS-enabled token server:
Step 1. | Before configuring Cisco Secure ACS, ensure that the RADIUS-enabled token server is installed and configured. |
Step 2. | From the ACS external database configuration menu, select RADIUS token server, and create a new token server as shown in Figures 10-3, 10-4, and 10-5. Figure 10-3. Configuring ACS for RADIUS-Enabled Token Server (Step 2)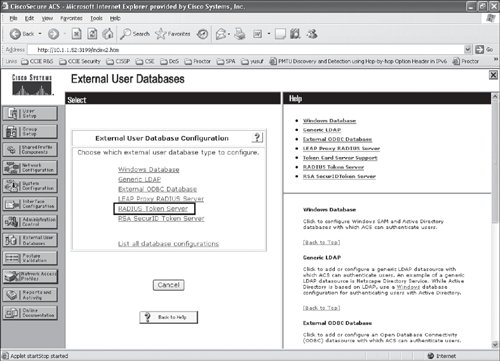
Figure 10-4. Configuring ACS for RADIUS-Enabled Token Server (Step 2 cont)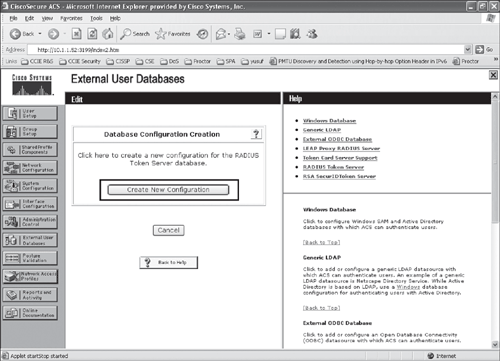
Figure 10-5. Configuring ACS for RADIUS-Enabled Token Server (Step 2 cont)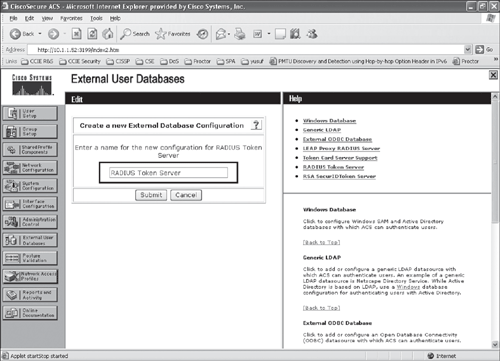
|
Step 3. | After the token server instance is created, select Configure to add the RADIUS parameters for the token server, as shown in Figures 10-6 and 10-7. Figure 10-6. Configuring ACS for RADIUS-Enabled Token Server (Step 3)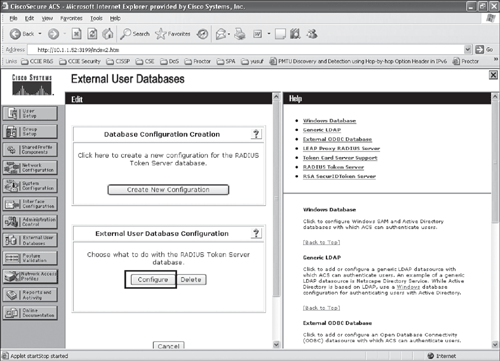
Figure 10-7. Configuring ACS for RADIUS-Enabled Token Server (Step 3 cont)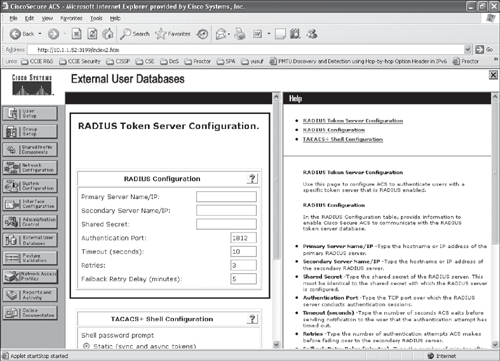
|
Step 4. | Configure the external database Unknown User Policy to select the RADIUS token server instance to handle authentication requests, as shown in Figures 10-8 and 10-9. Figure 10-8. Configuring ACS for Unknown User Policy (Step 4)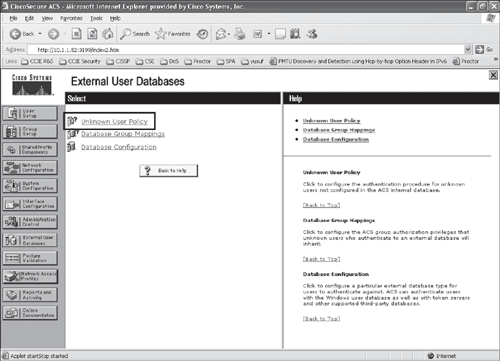
Figure 10-9. Configuring ACS for Unknown User Policy (Step 4 cont)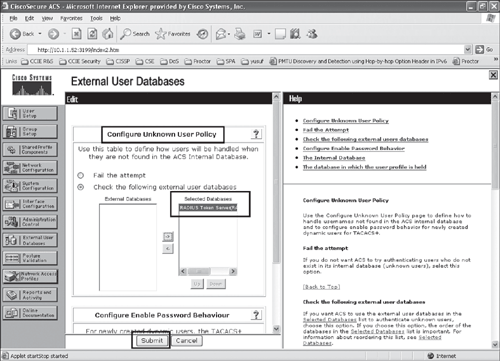
|
Tip
For more information on configuring a RADIUS-enabled token server on Cisco Secure ACS, refer to http://tinyurl.com/yu26nj.
You can find a sample configuration available at Cisco.com to configure Cisco Secure ACS with RSA SecurID (ACE Server) implementation:
The following options are available to install Cisco Secure ACS with RSA SecurID token server in these combinations:
The RSA SecurID server, RSA SecurID client, and ACS can be on the same server.
The RSA SecurID server can be on one server, and the RSA SecurID client with ACS can be on another server.
Tip
For more information on configuring the RSA SecurID Token Server on Cisco Secure ACS, refer to http://tinyurl.com/yu26nj.