The IEEE 802.1x port-based authentication solution can be deployed in two ways, as described in the sections that follow.
Figure 11-4 shows a point-to-point scenario connecting one client per port. The 802.1x configuration on the switch is port based and will allow one client to authenticate. When the client is powered up, the port link changes to an up state, and the port state is changed to an unauthorized state followed by 802.1x message exchange, as shown in Figure 11-2. If the client authentication is successful, the port transitions to an authorized state. If the client leaves or another client connects to the port, the switch changes the port status to down, and the port transitions to unauthorized state.
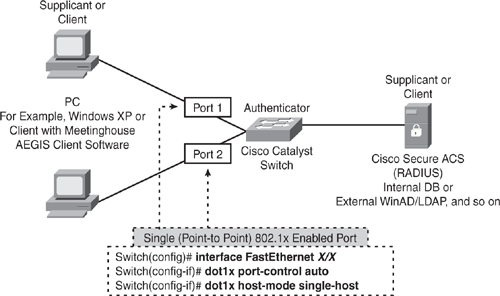
Figure 11-5 and Figure 11-6 show two separate scenarios for the 802.1x port-based authentication in a wireless LAN deployment.
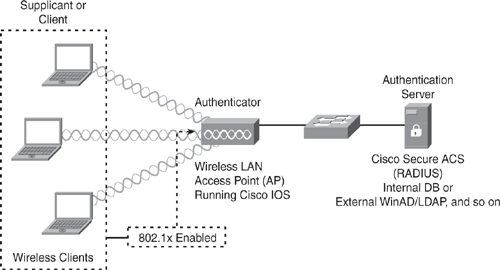
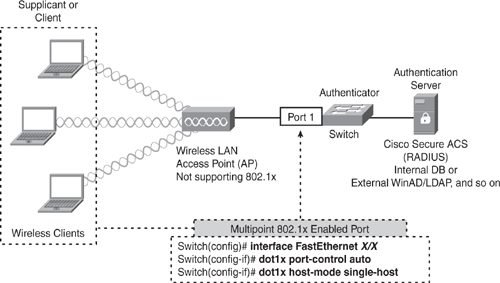
Figure 11-5 shows a wireless LAN access point (AP) that supports 802.1x (AP running Cisco IOS) acting as an authenticator for directly attached wireless clients.
Figure 11-6 shows a wireless LAN access point that does not support the 802.1x; hence, the 802.1x is implemented on the switch just like a point-to-multipoint connection where the switch acts as an authenticator.
In Figure 11-6, the port on the switch connecting the AP is configured as a multihost port for the 802.1x authentication. As soon as a wireless client host is successfully authenticated, the port transitions to the authorized state, and all other indirectly connected wireless hosts are also granted access. If the authenticated wireless client logs out or disconnects, the port will transition to the unauthorized state, and all other indirect hosts will also be disconnected. In this type of deployment, the AP is responsible for authenticating the directly connected clients, and the wireless access point acts as a client to the switch. This is not a very secure method and can lead to security holes because an unauthorized wireless client may get access without having to pass valid authentication. Chapter 12 covers WLAN security in greater detail.
Note
It is important to note that after the port has reached an authorized state, any number of clients that have Layer 2 connectivity can pass traffic through that port. However, this could be changed by using some of the advanced features in Cisco IBNS solution, such as MAC address filtering.