Day-zero attacks, viruses, and worms have become an increasing problem and continue to disrupt business operations. As discussed earlier, the most common issue on modern and open-standard networks is the security posture of internal endpoint devices that connect the network. Endpoints that do not comply with established security policies pose a threat and can introduce a security risk into the network. A network admission control (NAC) solution is needed to ensure that an endpoint is complying to predetermined security policies, such as the latest antivirus and operating system patches, thus preventing vulnerable and noncompliant hosts from obtaining network access.
On a regular network, the hosts are trusted to join the network, without requiring authentication. In an 802.1x protected network (non-NAC 802.1x), a host is allowed on the network after authentication through a password or certificate. However, no check is made to see whether that system is compliant with a corporate security policy to ensure that the host has the latest antivirus and operating system patches. NAC takes the additional step of having a service that validates the client's security posture prior to allowing the session to go into an authorized state.
With all the firewalls and integrated security devices, the noncompliant endpoint makes its way through the network. An infected host could immediately begin to spread a virus or worm throughout the network and potentially expose the network to various threats and attacks.
Figure 13-1 illustrates this very problem, in which an infected noncompliant host connects to the network, and potential infection spreads across the network. With an automated system such as NAC in place, the network can detect endpoints that are out of policy compliance before network access is granted. A noncompliant host that is out of compliance can be denied network access or quarantined so that remedial action can be taken. A potential threat is thwarted by preventing noncompliant endpoints from joining the network.
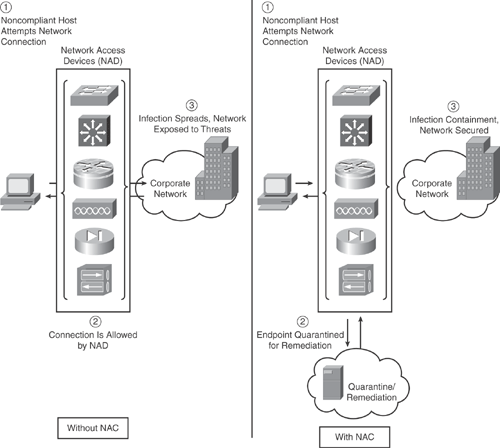
As shown in Figure 13-1, the NAC solution uses the network access devices (NAD) to protect the infrastructure from any endpoint seeking network access. Only compliant trusted endpoints are granted access. Noncompliant devices are denied access and quarantined for remediation. This policy compliance solution limits the potential damage from known and unknown security threats.
Cisco NAC is part of the Cisco SDN solution and is an initiative led by Cisco with the alliance of multiple vendors to enforce security policy compliance on all devices seeking network access. Cisco NAC enables the network to automatically identify, detect, and prevent emerging security threats. Cisco NAC is focused on proactive security solutions, thereby limiting damage from known and unknown threats from both internal and external sources.
Cisco offers NAC the solution in two forms:
Cisco NAC Appliance (formerly known as Cisco Clean Access): The NAC appliance solution is the most widely deployed solution and is based on the Cisco Clean Access (CCA) dedicated NAC appliance. The NAC appliance solution does not rely on partners and vendors because it offers self-contained endpoint assessment, policy management, and remediation services. NAC appliance accommodates most common scenarios, including LAN, WAN, wireless, and remote access. The NAC appliance is a Cisco packaged solution.
Cisco NAC Framework: The NAC framework solution uses the existing network infrastructure and third-party vendor solutions to enforce security policy compliance on all endpoints. The NAC framework is designed for highly specialized network environments where NAC intelligence is embedded in the network fabric. The NAC framework can be implemented on NAC-enabled network access devices (NAD) such as Cisco routers, switches, wireless access points, firewalls, and concentrators to grant access to compliant endpoints that are attempting to connect to the network. Noncompliance endpoints are placed in quarantine for remediation. The NAC framework solution does not require investment in new devices and utilizes existing investment in Cisco NADs. An overlay system is not required to perform admission control.
Figure 13-2 compares NAC appliance to NAC framework solution options.
The information in Figure 13-2 is taken from the Cisco general product presentation on "Cisco NAC Solution."
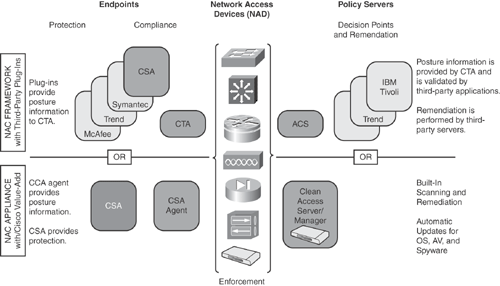
The multivendor NAC focuses on providing a framework for policy compliance-based access control.
Table 13-1 illustrates the different functions of a NAC environment.