Cisco NAC appliance (formerly known as Cisco Clean Access) is an end-to-end network registration and enforcement NAC solution that offers the identification, scanning, authentication, authorization, and remediation of wired, wireless, and remote users prior to allowing users onto the network.
The NAC appliance solution offers policy enforcement to all devices that are compliant with network security policy and repairs any vulnerability before granting network access.
Cisco NAC appliance engages at the point of authentication:
It recognizes an endpoint by a given device, user, and role within the network.
It evaluates whether endpoints are compliant with security policies and enforces security policies by blocking, isolating, and repairing noncompliant endpoints. Security policies can vary by user type, device type, or operating system.
It redirects endpoints into a quarantine area, where remediation occurs at the discretion of the administrator.
It applies posture assessment and remediation services to all devices, regardless of device type.
It enforces security policies on all networked devices, including Windows, Mac, and Linux laptops, desktops, PDAs, printers, and IP phones.
It applies admission control to devices connecting through the LAN, wireless LAN, WAN, or VPN connections.
The Cisco NAC appliance solution consists of the following three components:
Clean Access Manager: The Cisco Clean Access Manager is a web-based GUI application that is used to create security policies, establish roles, perform compliance checks, manage users, and define remediation rules.
Clean Access Manager: Communicates with the Cisco Clean Access Server, which is the primary component used for enforcement in the NAC appliance architecture. The Clean Access Manager can also be used as a proxy to the backend authentication servers.
The Cisco Clean Access Manager is available in three licensed options: the Cisco Clean Access Manager Lite, which is used to manage up to three Cisco Clean Access Servers; the standard Cisco Clean Access Manager, used to manage up to 20 Cisco Clean Access Servers; and the Cisco Clean Access Super Manager, which is used to manage up to 40 Cisco Clean Access Servers.
Clean Access Server: Clean Access Server is a network layer device that triggers assessment when users attempt network access and can enforce network access privileges based on endpoint compliance. The Clean Access server is primarily used as an enforcement device and can block users at the port layer, thereby restricting access to the trusted network until they pass the inspection successfully.
The Clean Access Server can be implemented either in-band or out-of-band, in Layer 2 or Layer 3 mode, and as a virtual gateway or as a real IP gateway. The Cisco Clean Access Server can be deployed locally or globally, at the edge or centrally.
The Cisco Clean Access Server is available in five sizes based on the number of online, concurrent users: 100, 250, 500, 1500, and 2500 users.
Clean Access Agent (optional): The Clean Access Agent (CAA) is a piece of lightweight read-only agent software, which runs on the client endpoint to provide posture information and streamlines remediation functions. It can perform inspection of the local host and provide information by analyzing Registry settings, services, and files. CAA can also determine whether a device has the required patches and hotfixes and whether it has the correct antivirus version and other installed security software, such as Cisco Security Agent (CSA).
Cisco Clean Access Agent is an optional component of the NAC Appliance solution and is distributed free of charge.
The Cisco NAC appliance can be deployed in several ways to accommodate various scenarios and possibilities. Table 13-2 illustrates various NAC Appliance deployment options.
| Deployment Model | Options |
|---|---|
| Passing Traffic Mode | Virtual gateway (bridged mode) Real IP gateway/NAT gateway (routed mode) |
| Physical Deployment Model | Edge Central |
| Client Access Mode | Layer 2 (client is adjacent to the NAC Appliance Server) Layer 3 (client is multiple hops from the NAC Appliance Server) |
| Traffic Flow Model | In-band (NAC Appliance Server is always inline with user traffic) Out-of-band (NAC Appliance Server is inline only during authentication, posture assessment, and remediation) |
| The information in Table 13-2 is taken from "Cisco NAC Appliance" data sheet at http://www.cisco.com/en/US/products/ps6128/products_data_sheet0900aecd802da1b5.html. | |
Figure 13-3 illustrates the Cisco NAC Appliance deployment in in-band mode. This mode works with any 802.11 wireless access point and is the preferred mode for VPN traffic.
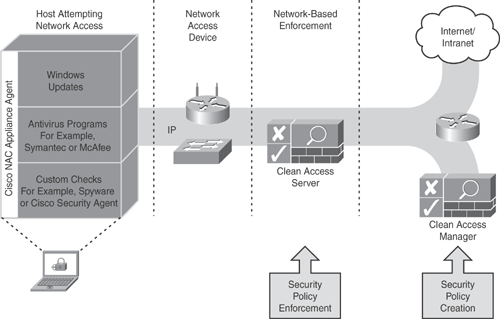
Figure 13-4 illustrates the Cisco NAC Appliance deployment in out-of-band mode. Note that the Clean Access Server will be in-band during the process of authentication, posture assessment, and remediation. After the user successfully passes these stages, all traffic traverses the switch port directly as out-of-band.
Figures 13-3 and 13-4 are taken from the "Cisco NAC Appliance" data sheet at http://www.cisco.com/en/US/products/ps6128/products_data_sheet0900aecd802da1b5.html.

Tip
Refer to the following URL for further information on the Cisco NAC Appliance solution: http://www.cisco.com/go/cca.