Cisco NAC Framework solution provides the same security policy enforcement framework as the Cisco NAC Appliance solution discussed previously. The main differentiator, which is Cisco NAC Framework, is an embedded approach that natively integrates into the existing infrastructure. It integrates using advanced security products and technologies, allowing networks to scale without making a significant investment.
Security point products only plug holes; they do not maintain network availability and resiliency. The Cisco NAC Framework solution offers proactive security architecture resulting in a resilient network infrastructure. The Cisco NAC Framework solution provides comprehensive and in-depth security defense to be built throughout the network infrastructure.
Cisco shares the NAC Framework program with third-party vendors, allowing them to integrate with Cisco NAC infrastructure to support the overall admission control solution. Participating with Cisco in this initiative are 90 leading vendors with solutions that include antivirus, remediation, client security, as well as management software manufacturers.
Partners participating in this program integrate security solutions that incorporate security features compatible with Cisco NAC infrastructure.
Note
Refer to the following Cisco URL for an updated list of Cisco NAC certified partners: http://www.cisco.com/web/partners/pr46/nac/partners.html.
The Cisco NAC Framework solution provides a policy enforcement mechanism for all endpoints that request network access, regardless of their access methods, ownership, device types, application configurations, and remediation models.
The Cisco NAC Framework solution is an architecture-based framework designed to take advantage of existing Cisco-based network technologies and existing deployments of security and management solutions from other manufacturers.
The Cisco NAC Framework triggers when a host attempts network access through any of the following:
Traffic triggers challenges on an endpoint that was installed with a Cisco Trust Agent (CTA). CTA is installed on an endpoint to gather client information, such as operating system version, patch and hotfix, and other software information.
EAP over UDP is used to exchange identity and authentication credentials between the endpoint and the NAD.
Credentials are forwarded to a Cisco Secure ACS (AAA server) via the RADIUS protocol.
A AAA server can optionally proxy the credentials to backend a third-party vendor server that is using the Host Credential Authorization Protocol (HCAP) and Generic Authorization Message Exchange (GAME) protocol for further compliance validation.
It evaluates whether endpoints are compliant with security policies (for example, antivirus DAT revision or OS patch version) and enforces security policies by blocking, isolating, and repairing noncompliant endpoints. Security policies can vary by user type, device type, antivirus type, or operating system.
The third-party vendor replies with compliance validation and verifies the posture.
The AAA server is configured with various authorization rule sets to respond to the respective posture validations.
Based on the endpoint identification, enforcement is accomplished on the NAD via the posture states (refer to Table 13-3) depending on the posture verification.
If the endpoint does not comply with the defined security policy, the Cisco NAC Framework redirects endpoints into a quarantine area, where remediation occurs at the discretion of the administrator.
NAC can enforce security policies on all networked devices, including Windows, Mac, and Linux laptops, desktops, PDA, printers, and IP phones.
NAC applies posture assessment and remediation services to all devices, regardless of device type.
Figure 13-5 illustrates the Cisco NAC Framework architecture and steps through the NAC flow.
The information in Figure 13-5 is taken from Cisco general product presentation on "Cisco NAC Solution."
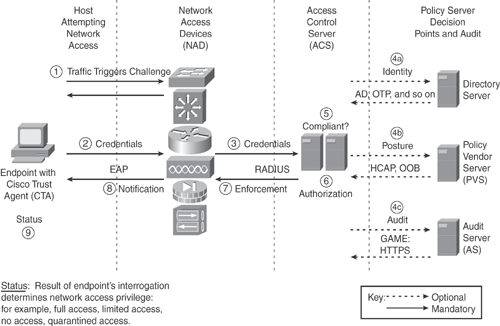
Table 13-3 lists various NAC posture states that are used for policy enforcement.
There are two methods of collecting information from an endpoint to perform a posture assessment:
In-band: The in-band method obtains application state via CTA, which collects state information from multiple software clients and forwards this information to the connected NAD where access control decisions are enforced.
Out-of-band: The out-of-band method is mainly used for NAH (NAC agentless hosts), which does not have CTA or any other tool that can collect state information from the endpoint. Out-of-band is the dynamic assessment of the endpoint. A good example of an agentless endpoint is a printer. Agentless hosts require IP connectivity to trigger NAC.
Protocols used in the NAC Framework solution include the following:
EAP (Extensible Authentication Protocol): EAP is used to exchange identity and credentials between the endpoint and the NAD. It supports a range of authentication methods. Some of the new extensions in EAP for NAC are EAP-TLV, Status Query, and EAP over UDP (EAPoUDP) (UDP port 21862), as shown in Figure 13-6.
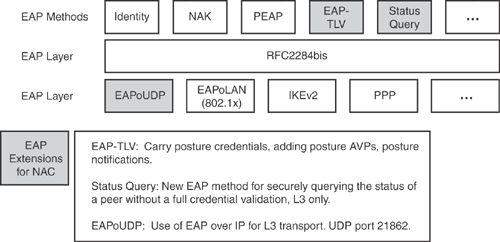
RADIUS (Remote Authentication Dial-In User Service): The RADIUS protocol is used to communicate between the NAD and a Cisco Secure ACS server.
HCAP (Host Credential Authorization Protocol): HCAP is used by Cisco Secure ACS to forward client credentials to third-party vendor servers and to receive posture token responses and optional notification messages from the vendor server. It uses an HTTP(S) session between ACS and vendor servers for EAP-based credentials.
GAME (Generic Authorization Message Exchange): Cisco Secure ACS triggers posture validation of NAH (NAC agentless host) by the vendor audit server and polls periodically for audit decision. The audit server responds with a posture state upon completion of the audit. It uses an HTTPS session between ACS and a vendor audit server, thereby extending Security Assertion Markup Language (SAML).
The four primary components of the NAC Framework solution are outlined in the following list:
Endpoint software: Endpoint security software includes products such as antivirus software, Cisco Security Agent (CSA), Personal Firewall, and the Cisco Trust Agent (CTA). The CTA is freely distributed software that is used to collect state information from multiple software clients, such as antivirus or any other installed security software. CTA forwards this information to the connected NAD, where access control decisions are enforced. Policy enforcement and admission control decisions are made on the basis of application and operating system status, such as antivirus and operating system patch levels. Cisco and NAC program partners integrate the CTA with their security software clients.
Network access devices (NAD): NAD is a Cisco Layer 2 or Layer 3 device that is used for policy enforcement and admission control based on endpoint compliance. NAD is primarily used as the enforcement device and can block users at Layer 2 and Layer 3, thereby allowing network access to the trusted endpoint and restricting or quarantining noncompliant endpoints.
Cisco NAC-enabled devices include Cisco routers, switches, wireless access points, and security appliances. These devices challenge endpoints for credentials and relay credential information to the access control server (AAA) and potential third-party policy servers, where admission control decisions are made. Based on the various defined policies, the NAD will enforce the appropriate posture states: permit, deny, quarantine, or restrict.
Access control and policy server: The access control (Cisco Secure ACS) and third-party vendor servers are responsible for evaluating the endpoint security information that is relayed from the Cisco NAD and determine the appropriate network access policy to be applied. Cisco Secure ACS server is used as the AAA server with the RADIUS protocol. ACS can proxy backend verification functions with third-party vendor policy servers that provide deeper credential validation capabilities, such as antivirus policy servers.
Management system: Cisco security management solutions provide the monitoring and reporting tools for the NAC Framework. Examples include CiscoWorks VPN/Security Management Solution (CiscoWorks VMS), CiscoWorks Security Information Manager Solution (CiscoWorks SIMS), and Cisco Security Manager (CSM) that are used for managing varied NAC-enabled devices. Cisco NAC cosponsors also provide various management solutions for their endpoint security software.
The Cisco NAC Framework solution provides support for the following Cisco NAC-enabled devices:
Cisco Routers—(Refer to Table 13-4)
| Supported Cisco Router Series | Supported Models | Operating System Image |
|---|---|---|
| Cisco 800 Series Routers | 831, 836, 837, and 870 Series | Cisco IOS 12.3(8)T or later |
| Cisco 1700 Series Routers | 1701, 1711, 1712, 1721, 1751, 1751-V, 1760 | Cisco IOS 12.3(8)T or later |
| Cisco 1800 Series Routers | 1841 | Cisco IOS 12.3(8)T or later |
| Cisco 2600 Series Routers | 2600XM, 2691 | Cisco IOS 12.3(8)T or later |
| Cisco 2800 Series Routers | 2801, 2811, 2821, 2851 | Cisco IOS 12.3(8)T or later |
| Cisco 3600 Series Routers | 3640/3640A, 3660-ENT Series | Cisco IOS 12.3(8)T or later |
| Cisco 3700 Series | 3725, 3745 | Cisco IOS 12.3(8)T or later |
| Cisco 3800 Series | 3845, 3825 | Cisco IOS 12.3(8)T or later |
| Cisco 7200 Series | All | Cisco IOS 12.3(8)T or later |
| Cisco 7500 Series | All | Cisco IOS 12.3(8)T or later |
| Cisco 7600 Series | All | Cisco IOS 12.3(8)T or later |
Cisco Catalyst switches—(Refer to Table 13-5)
| Switch Models | Supported Methods | Supervisor, if Applicable | Operating System Image |
|---|---|---|---|
| Cisco Catalyst 2940 | NAC-L2-802.1x | Not applicable | Cisco IOS Release 12.1(22)EA6 or later |
| Cisco Catalyst 2950 Cisco Catalyst 2955 | NAC-L2-802.1x | Not applicable | Cisco IOS Release 12.1(22)EA6 or later |
| Cisco Catalyst 2960 | NAC-L2-802.1x | Not applicable | Cisco IOS Release 12.2(25)SED or later |
| Cisco Catalyst 2970 | NAC-L2- 802.1x | Not applicable | Cisco IOS Release 12.2(25)SED or later |
| Cisco Catalyst 3550 | NAC-L2-IP NAC-L2- 802.1x | Not applicable | Cisco IOS Release 12.2(25)SED or later |
| Cisco Catalyst 3550 | NAC-L2-802.1x | Not applicable | Cisco IOS Release 12.1(22)EA6 or later |
| Cisco Catalyst 3560 | NAC-L2-IP NAC-L2-802.1x | Not applicable | Cisco IOS Release 12.2(25)SED or later |
| Cisco Catalyst 3750 | NAC-L2-IP NAC-L2-802.1x | Not applicable | Cisco IOS Release 12.2(25)SED or later |
| Cisco Catalyst 4500 | NAC-L2-IP NAC-L2-802.1x | Sup2+, 2-Plus-TS, Sup2+10GE, IV, V, V-10GE | Cisco IOS 12.2(25)SG or later |
| Cisco Catalyst 4900 | NAC-L2-IP NAC-L2-802.1x | Not applicable | Cisco IOS 12.2(25)SG or later |
| Cisco 6500 Series
Models: 6503, 6503-E, 6506, 6506-E, 6509, 6509-E, 6509-NEB, 6509-NEB-A, 651 | NAC-L2-IP | Supervisor 32, 720 | Cisco IOS 12.2(18)SXF2 |
| Cisco 6500 Series
Models: 6503, 6503-E, 6506, 6506-E, 6509, 6509-E, 6509-NEB, 6509-NEB-A, 651 | NAC-L2-IP NAC-L2- 802.1x | Supervisor 2, 32, 720 | Catalyst OS 8.5 or later |
VPN 3000 Series Concentrators—(Refer to Table 13-6)
| VPN Concentrator | Supported Models | Operating System Version |
|---|---|---|
| VPN 3000 series | 3005 to 3080 | Version 4.7 or later |
Cisco Unified Wireless Network—(Refer to Tables 13-8 and 13-9)
Cisco Security Agent (CSA)—v5.0 or later
Cisco Trust Agent (CTA)—v2.0 or later
CiscoSecure Access Control Server for Windows (ACS)—v4.0 or later
CiscoSecure Access Control Server Solution Engine (ACS)—v4.0 or later
Cisco Security Monitoring, Analysis, and Response System (MARS)
Table 13-4 lists Cisco routers that support the NAC L3 IP method (EAP over UDP). These are also referred to as the early NAC Release 1.0 devices.
Note
Cisco router models 1710, 1720, 1750, 26xx non-XM models, 3620, and 3660-CO do not support Cisco NAC. Also note that a specific Cisco IOS feature set is required to enable the Cisco NAC. Verify that the correct feature image is loaded on the supported hardware listed in Table 13-4.
Note
When NAC is enabled on a Cisco router, EAPoUDP is initiated from a router rather than the endpoint. Therefore, NAT issues may arise in which NAT is deployed between an endpoint and the router.
NAT implementations that depend on an endpoint having sent an EAPoUDP packet before forwarding an EAPoUDP request from the router are not supported. However, NAC and NAT can coexist on the same router.
NAC does not provide support when port address translation (PAT) is enabled between an endpoint and the router.
Table 13-5 lists Cisco switches that support either the NAC L2 IP method, which uses Extensible Authentication Protocol over User Data Protocol (EAP over UDP), or the NAC L2 802.1x (EAP over IEEE 802.1x) method. These are referred as the NAC Release 2.0 devices.
Table 13-6 lists the Cisco VPN 3000 series concentrator support for the NAC L3 IP method. NAC processing starts after an IPsec session is established. The VPN 3000-enabled NAC devices are referred to as the NAC Release 2.0 devices.
Note
At press time, the Cisco VPN 3000 concentrator supports L3 NAC IP for Remote Access sessions IPsec, SSL VPN, and L2TP over IPsec only. NAC does not apply to L2TP, PPTP, and LAN-to-LAN IPsec sessions.
The Cisco VPN 3000 Series Concentrators product is End-of-Sale and End-of-Life. For more details, refer to http://www.cisco.com/en/US/products/hw/vpndevc/ps2284/prod_eol_notice0900aecd805cd5a0.html.
Table 13-7 lists the Cisco Firewall Security Appliances that support the NAC L3 method.
Cisco NAC on the security appliances such as PIX 500 series and ASA 5500 series firewall appliances differs from NAC on Cisco IOS Layer 3 devices (such as routers) where routers trigger Posture Validation (PV) based on IP routed traffic. Cisco IOS-based NAD devices such as routers use an Intercept ACL to trigger Posture validation based on IP traffic, as shown in Example 13-1.
Cisco NAC on security appliance triggers Posture validation on IPsec VPN and SSL VPN sessions only. NAC on the security appliance does not support Layer 3 non-VPN traffic, IPv6 traffic, and security contexts.
Table 13-8 lists the Cisco wireless access points that support the NAC L2 802.1x method. These are referred to as the NAC Release 2.0 devices.
| Cisco Wireless Access Points | Supported Models | Operating System Image |
|---|---|---|
| 350 series | All | 12.3(7)JA1 or later |
| 1100 series | All | 12.3(7)JA1 or later |
| 1130 AG series | All | 12.3(7)JA1 or later |
| 1200 series | All | 12.3(7)JA1 or later |
| 1230 AG series | All | 12.3(7)JA1 or later |
| 1240 AG series | All | 12.3(7)JA1 or later |
| Table 13-9 lists the Cisco wireless LAN controllers that support the NAC L2 802.1X method. These are referred to as the NAC Release 2.0 devices. | ||
NAC framework can be deployed on various Cisco NAC-enabled devices, as previously discussed. NADs such as Cisco routers, switches, wireless access points, firewalls, and concentrators are used for enforcement to grant access to compliant endpoints that are attempting to connect to the network. Endpoints connecting from various scenarios including LAN, wireless LAN, WAN, and through VPN connections are supported by NAC Framework.
Figure 13-7 depicts various Cisco NAC Framework deployment scenarios.
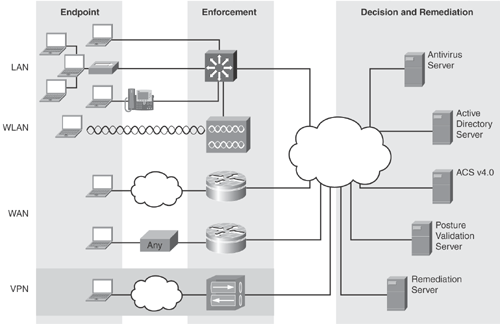
As discussed earlier, the NAC Framework can be deployed on various NAC-enabled devices for policy enforcement and network admission control.
Three primary methods for enforcing a security policy and performing admission control follow:
NAC-L3-IP: NAC-L3-IP is triggered on a Layer 3 device via IP packet. It uses EAPoUDP for posture and credentials. Enforcement is handled via per-host L3/L4 ACLs. The NAC-L3-IP solution can be implemented on Cisco routers, firewalls, and VPN concentrators.
NAC-L2-IP: NAC-L2-IP is triggered on a Layer 2 device via a DHCP or ARP request. It uses EAPoUDP for posture and credentials. Enforcement is done via per-host L3/L4 ACLs. The NAC-L2-IP solution can be implemented on Cisco switches (L2 switch-port).
NAC-L2-802.1x: NAC-L2-802.1x is triggered on a Layer 2 device via 802.1x. It leverages an existing 802.1x (EAP) L2 session to perform posture assessment and enforcement. Enforcement is done via dynamic VLAN assignment. The NAC-L2-802.1x solution can be implemented on Cisco switches (L2 switch-port) and wireless access points.
Figure 13-8 depicts various Cisco NAC Framework scenarios to perform admission control and enforcement points.
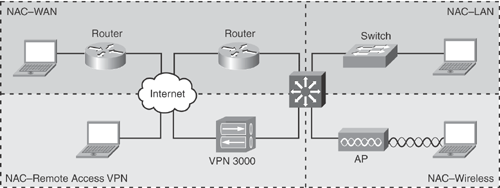
Table 13-10 shows the summary of features available in the three NAC Framework enforcement and admission control methods.
| Feature | NAC-L3-IP | NAC-L2-IP | NAC-L2-802.1x |
|---|---|---|---|
| Trigger mechanism | IP Packet | DHCP or ARP request | Data link up |
| Machine identity | N/A | N/A |  |
| User identity | N/A | N/A |  |
| Posture |  |  |  |
| VLAN assignment | N/A | N/A |  |
| URL-redirection |  |  | N/A |
| Downloadable ACLs |  |  | 6500-only (PBACLs) |
| Posture status queries |  |  | |
| 802.1x posture change | N/A | N/A |  |
Figure 13-9 shows various posture states (for example, Compliant, Noncompliant, Healthy, Quarantine) in NAC-L3-IP scenarios when a NAC-enabled device attempts a network connection:
NAC-Enabled: Health endpoints evaluated and granted normal access. Endpoint will still be reassessed to ensure continued compliance.
NAC-Enabled: Noncompliant endpoints placed in quarantine. This can also trigger remediation procedures. After remediation, reassessment will grant normal access.
NAC-Not-Enabled (Agentless): Device assessed via out-of-band audit passes and is granted normal access.
NAC-Not-Enabled (Agentless): Device assessed via out-of-band audit fails and is placed in quarantine or given no access.
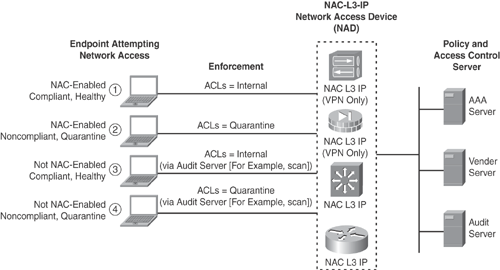
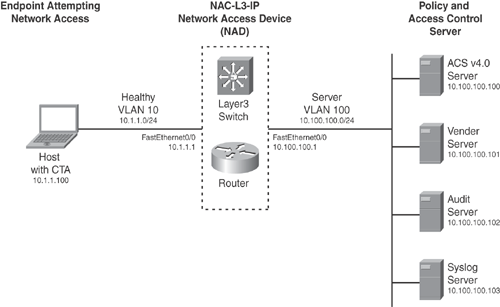
Figure 13-10 shows the topology diagram for the NAC-L3-IP sample configuration that is shown in Example 13-1, on a Cisco IOS-based device (for example, a router or Layer 3 switch) when a NAC-enabled device (with CTA) attempts network connection. NAC is triggered via an IP packet.
|
Code View: aaa new-model
aaa authentication eou default group radius
aaa authorization auth-proxy default group radius
aaa session-id common
!
ip admission name NAC-L3-IP eapoudp list EoU-Trigger-ACL #Define NAC trigger
!
Interface FastEthernet0/0
ip address 10.1.1.1 255.255.255.0
ip access-group Interface-ACL in
ip admission NAC-L3-IP
!
Interface FastEthernet0/1
ip address 10.100.100.1 255.255.255.0
!
ip access-list extended EoU-Trigger-ACL #NAC Trigger ACL
deny udp any any eq domain #allow DNS to bypass NAC
deny tcp any host 10.100.100.101 eq www #allow HTTP to bypass NAC
permit ip any any #all other IP traffic triggers NAC
!
ip access-list extended Interface-ACL
permit udp any any eq 21862 #permit EAPoUDP
permit udp any eq bootpc any eq bootps #permit DHCP
!
radius-server host 10.100.100.100 auth-port 1645 acct-port 1646
radius-server key cisco123
radius-server vsa send authentication #Enable VSAs
ip radius source-interface FastEthernet0/0
!
eou timeout hold-period 60 #Delay re-EAP after EAP failure
eou timeout revalidation 60 #Timeout to re-check all credentials
#ACS can override, enforces policy changes
eou timeout status-query 60 #How often check for status changes
ip auth-proxy inactivity-timer 60 #Equivalent to EoU revalidation timer
!
eou allow clientless #Permit agentless hosts, used for auditing
!
ip http server #IOS web server required for URL redirection
ip http authentication aaa #Enable auth-proxy
ip http secure-server #SSL
!
eou logging #Enable EAPoUDP logging
logging 10.100.100.103
!
|
Figure 13-11 shows various posture states (for example, Compliant, Noncompliant, Healthy, Quarantine) in NAC-L2-IP scenarios when a NAC-enabled device attempts network connection:
NAC-Enabled: Health endpoints evaluated and granted normal access. Endpoint will still be reassessed to ensure continued compliance.
NAC-Enabled: Noncompliant endpoints placed in quarantine. This can also trigger remediation procedures. After remediation, reassessment will grant normal access.
NAC-Not-Enabled (Agentless): Device assessed via out-of-band audit passes and is granted normal access.
NAC-Not-Enabled (Agentless): Device assessed via out-of-band audit fails and is placed in quarantine or given no access.
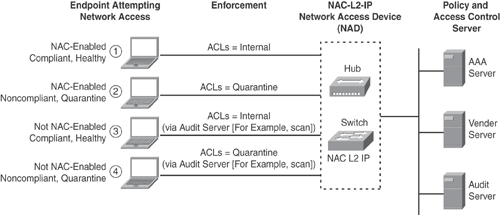
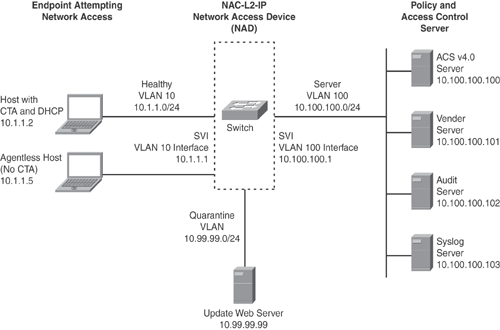
Figure 13-12 shows the topology diagram for a NAC-L2-IP sample configuration. Example 13-2 is the configuration on a Catalyst switch when a NAC-enabled device (with and without CTA) attempts network connection. NAC is triggered via ARP or DHCP packet. Layer 2 switches do not have intercept ACLs; they use port ACLs.
|
Code View: hostname sw-3550
!
aaa new-model
aaa authentication eou default group radius
aaa authorization auth-proxy default group radius
aaa session-id common
!
ip subnet-zero
ip routing
no ip domain-lookup
!
ip admission name NAC-L2-IP eapoudp #Define NAC policy
ip admission name NAC-L2-IP-Bypass eapoudp bypass
!
ip dhcp excluded-address 10.1.1.1 10.1.1.5
ip dhcp pool my_dhcp_pool
network 10.1.1.0 255.255.255.0
default-router 10.1.1.1
lease 3
!
ip dhcp snooping vlan 10 #Optional—Enable DHCP snooping on VLAN 10
ip device tracking #Build IP device table from ARP requests
!
vtp domain cisco
vtp mode transparent
!
identity profile eapoudp
device authorize ip-address 10.1.1.5 policy AgentlessHost_Profile
identity policy AgentlessHost_Profile
access-group AgentlessHost_ACL
redirect url http://10.99.99.99 match Quarantine_URL_Redir_ACL
!
vlan 10
name healthy
!
vlan 99
name quarantine
!
vlan 100
name server
!
interface FastEthernet0/1
switchport mode access
switchport access vlan 10
ip access-group Interface-ACL in
ip admission NAC-L2-IP
!
ip access-list extended Interface-ACL
permit udp any any eq 21862 #permit EAPoUDP
permit udp any eq bootpc any eq bootps #permit DHCP
permit udp any any eq domain #permit DNS
permit tcp any host 10.99.99.99 eq www #permit HTTP access to update server
permit icmp any any #permit ICMP for testing
deny ip any any #Implicit Deny
!
ip access-list extended AgentlessHost_ACL
permit ip any any
!
ip access-list extended Quarantine_URL_Redir_ACL
deny tcp any host 10.99.99.99 eq www
permit tcp any any eq www
!
radius-server attribute 8 include-in-access-req
radius-server host 10.100.100.100 auth-port 1645 acct-port 1646
radius-server key cisco123
radius-server vsa send authentication #Enable VSAs
!
eou allow ip-station-id
eou timeout hold-period 60 #Delay re-EAP after EAP failure
eou timeout revalidation 60 #Timeout to re-check all credentials
#ACS can override, enforces policy changes
eou timeout status-query 60 #How often check for status changes
ip auth-proxy inactivity-timer 60 #Equivalent to EoU revalidation timer
!
eou allow clientless #Permit agentless hosts, used for auditing
!
interface Vlan10
ip address 10.1.1.1 255.255.252.0
!
interface Vlan99
ip address 10.99.99.1 255.255.252.0
!
interface Vlan100
ip address 10.100.100.1 255.255.252.0
!
ip classless
ip http server
ip http secure-server
!
eou logging #Enable EAPoUDP logging
logging 10.100.100.103
!
|
Figure 13-13 shows various posture states (for example, Compliant, Noncompliant, Healthy, Quarantine) in NAC-L2-802.1x scenarios when a NAC-enabled device attempts network connection:
NAC-Enabled: Healthy endpoints evaluated and granted normal access. Endpoint will still be reassessed to ensure continued compliance.
NAC-Enabled: Healthy endpoints evaluated and granted normal access. IP phones are not impacted when NAC is performed on endpoints when VVID is used on the switch.
NAC-Enabled: Noncompliant endpoints placed in quarantine. This can also trigger remediation procedures. After remediation, reassessment will grant normal access.
NAC-Not-Enabled: Known (Agentless) device. Predefined exception rules to grant access.
NAC-Not-Enabled: Known (Agentless) visitor device. Visitor and Agentless devices may be given partial or no access (for example, visitor fails authentication and is placed in GUEST VLAN).
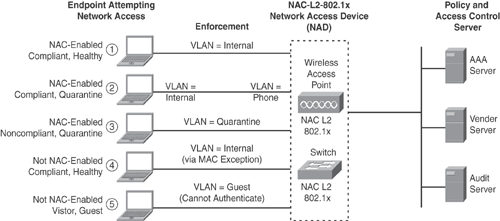
Example 13-3 shows a sample configuration for NAC-L2-802.1x on a Catalyst switch when a NAC-enabled device (with CTA) attempts network connection. NAC-L2-802.1x leverages the existing 802.1x (EAP) L2 session to perform posture assessment and enforcement. NAC is triggered when the data link state goes up after a host is powered on.
AAA authorization must be configured on the switch if network-related services such as a per-user VLAN assignment on 802.1x authenticated ports are required. The following three RADIUS attributes (attribute 64, 65, and 81) must be returned to the switch for 802.1x authentication:
[RADIUS Attribute 64] Tunnel-Type = VLAN
RADIUS attribute [64] must contain the value "VLAN" (type 13).
[RADIUS Attribute 65] Tunnel-Medium-Type = 802
Attribute [65] must contain the value "802" (type 6).
[RADIUS Attribute 81] Tunnel-Private-Group-ID = VLAN NAME
Attribute [81] contains the VLAN name or VLAN ID assigned to the authenticated user.
|
Code View: hostname Sw-3550 ! aaa new-model aaa authentication dot1x default group radius aaa authorization network default group radius aaa accounting dot1x default start-stop group radius aaa accounting network default start-stop group radius ! ip dhcp snooping vlan 10 ip device tracking vtp domain cisco vtp mode transparent ! dot1x system-auth-control ! vlan 10 name healthy ! vlan 99 name quarantine ! vlan 100 name server ! interface FastEthernet0/1 switchport mode access switchport access vlan 10 dot1x pae authenticator dot1x port-control auto dot1x reauthentication ! radius-server host 10.100.100.100 auth-port 1645 acct-port 1646 radius-server key cisco123 radius-server vsa send authentication ! |
The Cisco NAC Framework solution provides a scalable architecture with a centralized policy and a distributed enforcement component, with robust integration with Cisco security products and technologies.
Cisco NAC fundamentally changes how networks are secured with a strong access level that results in a proactive security model that was not available before.
Note
Refer to the NAC Framework URL for further information on the Cisco NAC Framework solution: http://www.cisco.com/en/US/netsol/ns617/networking_solutions_sub_solution_home.html.