PKI is a framework that provides a mechanism to securely issue and distribute public keys. PKI arrangement enables the transmission of secure data over insecure public networks by using trusted public and private cryptographic key pairs, which are obtained and shared through a trusted authority.
PKI provides a digital certificate that can identify an individual or an organization by binding of public keys to users. When used in IPsec VPN, PKI provides authentication, nonrepudiation, and confidentiality services.
PKI consists of various protocols, services, and standards that support applications of the public key infrastructure.
The public key infrastructure assumes the use of the public key cryptography system, also known as asymmetric cryptography, which is based on two-key pairs: one key for encryption and another for decryption. Asymmetric cryptography standards and protocols are covered in greater detail in Chapter 14.
PKI components include the following:
Digital certificate (also known as identity certificate): A digital certificate uses a digital signature to bind a public key with a user's identity to produce a public key certificate. A certificate contains information, such as the certificate validity period, peer identity information, encryption keys that are used for secure communications, and the signature of the issuing CA. A certificate is a digital equivalent of a passport.
Certificate Authority (CA): A CA is the major component in the PKI system. The CA issues and verifies digital certificates. A certificate includes the public key that is bound to a user identity. A CA is also known as a trustpoint, which manages certificate requests and issues certificates to participating network devices. Many vendors offer CA Server solutions, including Cisco. The Cisco IOS Router can be configured as the certificate server. CA implementation can be either an in-house implementation or be outsourced.
Registration Authority (RA)(optional): RAs provide an interface between the user and the CA. The RA acts as the verifier for the certificate authority before a digital certificate is issued to a requestor.
Directory service: The certificates with their public keys are held in directory services.
Certificate Revocation List (CRL): The CRL is a list of serial numbers of revoked certificates. A CA revokes certificates that are no longer used and publishes the CRL.
Simple Certificate Enrollment Protocol (SCEP): SCEP is a Cisco proprietary certificate enrollment protocol used on network devices to obtain digital certificates from the CA server. SCEP uses HTTP to communicate with the CA or RA. SCEP is the most commonly used method for sending and receiving requests and certificates.
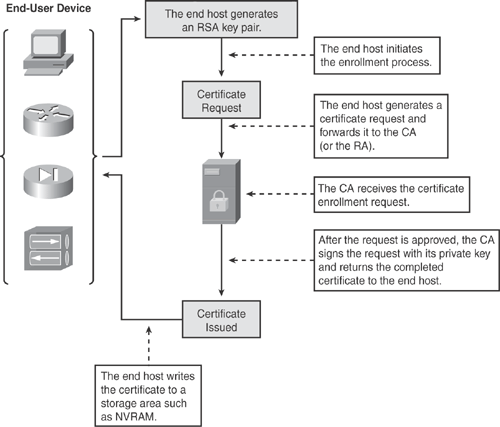
Certificate enrollment is the process of obtaining a certificate from a CA server. Each peer participating in the PKI must enroll with a CA. A number of methods are available for certificate enrollment, such as SCEP, PKCS12, IOS File System (IFS), and Manual (cut-and-paste). Figure 15-15 illustrates the certificate enrollment process.
Tip
Refer to this Cisco documentation URL to learn more about certificate enrollment for a PKI and the methods available for certificate enrollment: http://www.cisco.com/en/US/products/ps6350/products_configuration_guide_chapter09186a00804a5a17.html.
The format of a public key certificate is defined by the ITU-T based X.509 standard for a public key infrastructure. The structure format of an X.509 v3 digital certificate contains the following elements:
Version
Serial Number
Algorithm ID
Issuer
Validity
Subject
Subject Public Key Info
Issuer Unique Identifier (Optional)
Subject Unique Identifier (Optional)
Extensions (Optional)
Certificate Signature Algorithm
Certificate Signature
Example 15-1 shows a standard X.509 v3 certificate.
|
Code View: Version: 3 (0x2)
Serial Number: 2 (0x2)
Signature Algorithm: shaWithRSAEncryption
Issuer: CN=ca
Validity
Not Before: Nov 19 02:41:41 2004 GMT
Not After : Nov 19 02:41:41 2007 GMT
Subject: CN=myRouter.cisco.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
00:94:a8:db:8d:f5:9b:21:c4:47:de:9e:db:84:32:
b3:f0:ff:f2:30:dc:82:05:0e:4c:19:a8:0b:7c:d1:
04:3e:82:b6:8d:5c:e6:59:0a:26:23:f5:23:41:78:
75:cf:03:2e:52:45:e7:2d:4a:78:08:29:ea:8a:44:
e5:96:ea:b6:2f:7b:71:14:3d:ec:33:b2:cd:75:01:
49:14:da:72:9c:25:6e:72:a0:aa:60:85:37:2e:57:
f0:2f:c5:c6:e3:57:17:b2:7a:fd:fb:58:98:2f:5f:
9e:22:dd:62:f8:55:fa:74:fd:3e:38:66:e7:d9:78:
df:f0:c1:a0:ae:f3:9c:e1:39
Exponent: 65537 (0x10001)
71:b1:a5:01:ad:fb:73:20:57:57:b0:54:fc:04:2e:5e:31:ae:69:40:c0:
cf:93:b4:7a:5f:[........]
|
Tip
In Chapter 14, Figure 14-4 depicts how the asymmetric key encryption process works as it uses the two keys known as public and private keys. Figure 14-6 in Chapter 14 illustrates how the cryptographic keyed-hash algorithm works.
Table 15-7 exemplifies the use of public and private keys in the PKI framework.
| Function | Key-type |
|---|---|
| To send an encrypted message | Use the receiver's public key |
| To decrypt an encrypted message | Use the receiver's private key |
| To send an encrypted signature | Use the sender's private key |
| To decrypt an encrypted signature (and authenticate the sender) | Use the sender's public key |