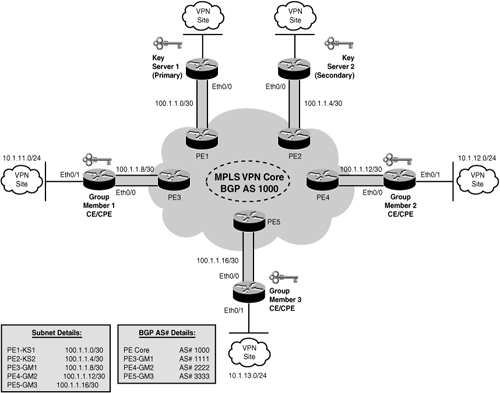
Based on the illustration shown in Figure 17-6, the following configuration examples provide deployment guidelines for implementing a Cisco IOS GET VPN solution in an any-to-any design, thereby offering end-to-end CE-CE encryption in an MPLS VPN network environment.
Example 17-1 shows the Key-Server-1 configuration.
Example 17-2 shows the Key-Server-2 configuration.
Example 17-3 shows the Group-Member-1 configuration.
Example 17-4 shows the Group-Member-2 configuration.
Example 17-5 shows the Group-Member-3 configuration.
The topology shown in Figure 17-6 is used in Examples 17-1 through 17-5 to demonstrate an intranet VPN scenario. The MPLS VPN core interconnects VPN sites as shown in Figure 17-6. The CE/CPE routers (Group Members 1 through 3) on each VPN site are grouped into a single GDOI group that correlates with the VPN of which these sites are a part. All the key servers and group members are part of the same VPN. Key-Server-1 is the primary key server and Key-Server-2 is the secondary key server.
|
Code View: hostname KeyServer-1 ! <..> ! crypto isakmp policy 10 encr 3des authentication pre-share group 2 ! crypto isakmp key cisco address 100.1.1.5 crypto isakmp key cisco address 100.1.1.9 crypto isakmp key cisco address 100.1.1.13 crypto isakmp key cisco address 100.1.1.17 ! crypto ipsec transform-set mygdoi-trans esp-3des esp-sha-hmac ! crypto ipsec profile gdoi-profile-getvpn set security-association lifetime seconds 1800 set transform-set mygdoi-trans ! crypto gdoi group getvpn identity number 1234 server local rekey lifetime seconds 86400 rekey retransmit 10 number 2 rekey authentication mypubkey rsa getvpn-export-general rekey transport unicast sa ipsec 1 profile gdoi-profile-getvpn match address ipv4 199 replay counter window-size 64 replay time window-size 5 address ipv4 100.1.1.1 redundancy local priority 100 peer address ipv4 100.1.1.5 ! interface Ethernet0/0 description Outside interface to PE1 ip address 100.1.1.1 255.255.255.252 ! ip classless ip route 0.0.0.0 0.0.0.0 100.1.1.2 ! access-list 199 remark ACL policies to be pushed to authenticated group members access-list 199 permit ip 10.1.0.0 0.0.255.255 10.1.0.0 0.0.255.255 ! <..> |
|
Code View: hostname KeyServer-2 ! <..> ! crypto isakmp policy 10 encr 3des authentication pre-share group 2 ! crypto isakmp key cisco address 100.1.1.1 crypto isakmp key cisco address 100.1.1.9 crypto isakmp key cisco address 100.1.1.13 crypto isakmp key cisco address 100.1.1.17 ! crypto ipsec transform-set mygdoi-trans esp-3des esp-sha-hmac ! crypto ipsec profile gdoi-profile-getvpn set security-association lifetime seconds 1800 set transform-set mygdoi-trans ! crypto gdoi group getvpn identity number 1234 server local rekey lifetime seconds 86400 rekey retransmit 10 number 2 rekey authentication mypubkey rsa getvpn-export-general rekey transport unicast sa ipsec 1 profile gdoi-profile-getvpn match address ipv4 199 replay counter window-size 64 replay time window-size 5 address ipv4 100.1.1.5 redundancy local priority 75 peer address ipv4 100.1.1.1 ! interface Ethernet0/0 description Outside interface to PE2 ip address 100.1.1.5 255.255.255.252 ! ip classless ip route 0.0.0.0 0.0.0.0 10.1.1.6 ! access-list 199 remark ACL policies to be pushed to authenticated group members access-list 199 permit ip 10.1.0.0 0.0.255.255 10.1.0.0 0.0.255.255 ! <..> |
|
Code View: hostname GroupMember-1 ! <..> ! crypto isakmp policy 10 encr 3des authentication pre-share group 2 ! crypto isakmp key cisco address 100.1.1.1 crypto isakmp key cisco address 100.1.1.5 ! crypto gdoi group getvpn identity number 1234 server address ipv4 100.1.1.1 server address ipv4 100.1.1.5 ! crypto map getvpn-map 10 gdoi set group getvpn ! interface Ethernet0/0 description Outside interface to PE3 ip address 100.1.1.9 255.255.255.252 crypto map getvpn-map ! interface Ethernet0/1 description Inside interface ip address 10.1.11.1 255.255.255.0 ! router bgp 1111 no synchronization bgp log-neighbor-changes network 10.1.11.0 mask 255.255.255.0 neighbor 100.1.1.10 remote-as 1000 no auto-summary ! <..> |
|
Code View: hostname GroupMember-2 ! <..> ! crypto isakmp policy 10 encr 3des authentication pre-share group 2 ! crypto isakmp key cisco address 100.1.1.1 crypto isakmp key cisco address 100.1.1.5 ! crypto gdoi group getvpn identity number 1234 server address ipv4 100.1.1.1 server address ipv4 100.1.1.5 ! crypto map getvpn-map 10 gdoi set group getvpn ! interface Ethernet0/0 description Outside interface to PE4 ip address 100.1.1.13 255.255.255.252 crypto map getvpn-map ! interface Ethernet0/1 description Inside interface ip address 10.1.12.1 255.255.255.0 ! router bgp 2222 no synchronization bgp log-neighbor-changes network 10.1.12.0 mask 255.255.255.0 neighbor 100.1.1.14 remote-as 1000 no auto-summary ! <..> |
|
Code View: hostname GroupMember-3 ! <..> ! crypto isakmp policy 10 encr 3des authentication pre-share group 2 ! crypto isakmp key cisco address 100.1.1.1 crypto isakmp key cisco address 100.1.1.5 ! crypto gdoi group getvpn identity number 1234 server address ipv4 100.1.1.1 server address ipv4 100.1.1.5 ! crypto map getvpn-map 10 gdoi set group getvpn ! interface Ethernet0/0 description Outside interface to PE5 ip address 100.1.1.17 255.255.255.252 crypto map getvpn-map ! interface Ethernet0/1 description Inside interface ip address 10.1.13.1 255.255.255.0 ! router bgp 3333 no synchronization bgp log-neighbor-changes network 10.1.13.0 mask 255.255.255.0 neighbor 100.1.1.18 remote-as 1000 no auto-summary ! <..> |
The following show commands can be used to verify functionality on key-server (ks) and group-members (gm).
show crypto isakmp sa
show crypto gdoi
show crypto gdoi ks acl
show crypto gdoi ks members
show crypto gdoi ks policy
show crypto gdoi ks rekey
show crypto gdoi ks replay
show crypto gdoi ks coop
show crypto session detail
show crypto gdoi gm acl
show crypto gdoi gm rekey
show crypto gdoi gm replay