VPN technologies in recent years have evolved and have been widely used to provide secure connectivity, extending the reach of networks. As discussed in Chapter 15, "IPsec VPN," two primary methods are used to deploy Remote Access VPN technology:
Remote Access: IPsec VPN (covered in Chapter 15)
Remote Access: SSL VPN
Cisco IPsec VPN and SSL VPN are complementary technologies. Both solutions offer remote access connectivity and can be deployed together or individually to better address the deployment requirements. Selecting the appropriate method depends on the deployment requirements and the network architecture.
Table 18-1 shows a comparison summary between IPsec VPN and SSL VPN technologies that can assist you in evaluating the appropriate Remote Access VPN technology as needed.
| IPsec VPN | SSL VPN | |
|---|---|---|
| End-User System Options | Enables access primarily from company-managed desktops. | Enables access from company-managed, employee-owned, contractor or business partner desktops, Internet cybercafé, as well as hotspots. |
| End-User Access Method | Initiated using a preinstalled VPN client software. | Initiated through a web browser. |
| End-User System Software Requirements | Requires proprietary preinstalled client software. | Requires no special-purpose desktop VPN client software; only a web browser is required. |
| Software Updates | Can automatically update, but is more intrusive and requires user input. | No special-purpose desktop software installed; thus no updates are required. Note that full network application access is provided through software that dynamically installs and updates without user intervention. |
| Customized User Access | Offers granular access policies, but no web portals. | Offers granular access policies, as well as user-customized web portals. |
| Note: The information in Table 18-1 is compiled from a Cisco white paper on "Remote Access VPN for Secure Communications" at http://www.cisco.com/en/US/netsol/ns340/ns394/ns171/ns125/networking_solutions_white_paper0900aecd804fb79a.shtml. | ||
SSL VPN is an emerging technology offering a flexible, low-cost Internet-based remote solution by using the native SSL encryption of a web browser. SSL VPN does not require a special-purpose client software to be preinstalled on the system, thus enabling a user to connect from any computer, whether it is a company-managed or a non-company-managed system, such as a personal laptop, cybercafé, or home PC. SSL VPN sessions can be established from any Internet-enabled computer, thereby extending network access when and where required.
The Cisco SSL-based Remote Access VPN solution is a powerful tool that provides users with a virtual environment that emulates the working conditions of a main office with no geographical boundaries.
The Cisco Remote Access VPN solutions offer both IPsec VPN and SSL VPN technologies integrated on a single platform with unified management. The Cisco security solutions group offers the SSL VPN solution as part of the security products range. Examples include Cisco Integrated Services Routers (ISR), VPN Security, and Firewall Appliances.
Note
The Cisco SSL VPN solution is also commonly known as the Cisco WebVPN solution, and the two terms are interchangeably used in publications.
SSL VPN technology offers a wide range of benefits. Key features include the following:
Does not require special-purpose desktop VPN client software to be preinstalled on the system.
Uses a standard web browser to establish a remote access VPN connection.
Uses the native SSL encryption of a web browser to provide data confidentiality.
Enables additional client-server applications to be downloaded dynamically with multiple delivery methods to help ensure transparent download and distribution with Java, ActiveX, or .exe files.
Offers flexibility to establish VPN connections from any Internet-enabled system, be it a company-managed or non-company-managed system.
Allows easy firewall and network traversal from any location.
Offers enhanced security using the integrated Cisco IOS Firewall feature.
Figure 18-1 illustrates the concept of SSL VPN and how a remote access user can access protected resources via the Internet over a secure encrypted channel.
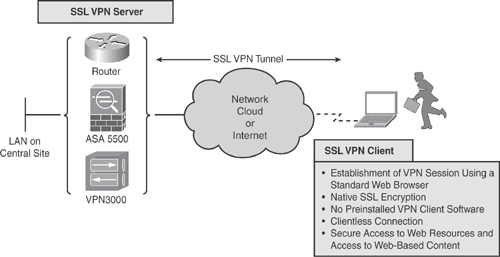
Note
As the industry leader in innovation, Cisco introduced the first-ever router platform to integrate the SSL VPN solution in Cisco IOS Software on Cisco Integrated Services Routers (ISR) series. The Cisco SSL VPN solution is also known as Cisco WebVPN.
SSL VPN is an enhanced Cisco Remote Access VPN solution that offers data confidentiality by using the native SSL encryption technology within a web browser. Table 18-2 summarizes the characteristics that need to be considered when evaluating the SSL VPN deployment option.
| Characteristics | IPsec VPN | SSL VPN |
|---|---|---|
| Anywhere access from non-company-managed systems, such as an employee-owned desktop, a personal laptop, cybercafés, and hotspots | X | |
| Business partner access | X | |
| User-customized web portals | X | |
| Minimized desktop support and software distribution | X | |
| Flexibility to the end users | X | X |
| VPN client customizability | X | |
| Capability to maintain existing IT deployment and support processes | X | |
| The information in Table 18-2 is compiled from the Cisco white paper on "Remote Access VPN for Secure Communications" at http://www.cisco.com/en/US/netsol/ns340/ns394/ns171/ns125/networking_solutions_white_paper0900aecd804fb79a.shtml. | ||
SSL VPN can be deployed in one of the following three access modes, as illustrated in Figure 18-2:
Clientless mode (Layer 7): Clientless mode provides secure access to web resources and access to web-based content. This mode is useful for accessing content that can be accessed in a web browser, such as Internet access, databases, and online web-based tools. Clientless mode can also offer remote file sharing by using the common Internet file system (CIFS) that provides a list of file server links in the web portal page, thereby allowing the remote user to browse listings of domains, servers, and directory folders, download a file, create a new file/directory, and so on. Clientless mode is limited to web-based content only.
Thin client mode (Layer 7) (also known as port forwarding): Thin client mode provides remote access to TCP-based services such as Post Office Protocol (POP3), Simple Mail Transfer Protocol (SMTP), Internet Message Access Protocol (IMAP), Telnet, and Secure Shell (SSH) applications. The thin client is delivered via a Java applet that is dynamically downloaded from the SSL VPN appliance upon session establishment. This mode extends the capability of the cryptographic functions of the web browser.
Thick client mode (Layer 3) (also known as tunnel mode or full tunneling client): The thick client mode provides remote access to an extensive array of application support and is delivered dynamically by downloading SSL VPN Client (SVC) software or the Cisco AnyConnect VPN client software from the VPN server appliance. This mode delivers a lightweight, centrally configured, and easy-to-support SSL VPN tunneling client that provides full network layer (Layer 3) access to virtually any application.
The information in Figure 18-2 is taken from the Cisco configuration guide on "Cisco IOS Software Releases 12.4T - SSL VPN" at http://www.cisco.com/en/US/products/ps6441/products_feature_guide09186a00805eeaea.html#wp1053878.
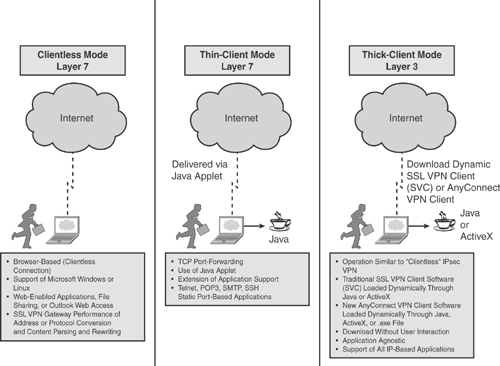
Figure 18-2 illustrates the basic SSL VPN access modes that were discussed previously.
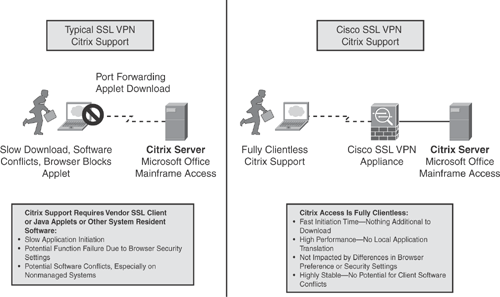
The Cisco SSL VPN solution also offers clientless Citrix support that allows Citrix clients to use applications running on a remote Citrix server as if they were executed locally on the internal LAN.
Clientless SSL VPN is commonly used for remote access to Citrix applications. One of the major advantages of using the Cisco SSL VPN solution is that no additional helper applications are required for Citrix access over clientless SSL VPN, which helps ensure fast application initiation time and reduces the risk of desktop software conflicts. Many other SSL VPN solutions on the market require proprietary applets to be pushed down for Citrix to function.
Figure 18-3 illustrates Citrix support comparison with a traditional SSL VPN and the Cisco SSL VPN solution.
The information concept in Figure 18-3 is taken from the Cisco Networkers session presentation# SEC-2010 – "Deploying Remote Access IPSec and SSL VPNs."