Security enforcement evolves mainly at the network level through common techniques such as authentication, integrity mechanisms, firewalls, and encryption technologies. These techniques are adopted to provide the desired security at the network level, where data is transitional. An important area that is largely overlooked in enforcing security is the host level—the endpoint, where data resides and the potential for damage is the greatest.
The Cisco Host Intrusion Prevention solution provides self-defending solutions by deploying intelligent agents on desktops and servers that defend against the proliferation of attacks across networks.
This chapter provides details on the Cisco Host-based Intrusion Prevention solution that uses Cisco Security Agent (CSA). The chapter takes a closer look at core concepts such as CSA architecture, CSA components, CSA Policies, Rules, CSA Rule Modules, and details on managing and deploying CSA using CSA Management Center (CSA MC).
Today in many ways, networks are overgrown and distributed in nature. With open network policies, enforcing security at the network perimeter is insufficient. Data needs to be secured where it resides—at the endpoints.
Traditionally, endpoint security has always taken a reactive approach by implementing antivirus, scanners, personal firewalls, and other system audit programs. These products usually rely on signature-based mechanisms to detect only the known vulnerabilities and intrusions. Signatures and virus definition files are core elements of these solutions.
With endpoint security, multiple products are required to combat different aspects of the issue. For example, a desktop host may require antivirus software and a personal firewall, along with a system audit program, to cover different aspects of the intrusion. This is not a scalable solution and creates manageability issues and an administrative burden.
Figure 21-1 illustrates the five phases of the host-based attack landscape and the life cycle of activities that take place when a host intrusion occurs.
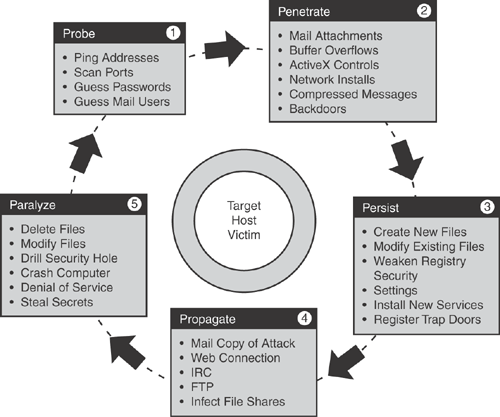
Viruses and worms take advantage of numerous vulnerabilities at the operating system and application level. New viruses and worms proliferate in no time and spread rapidly, infecting the host system. A signature-based approach cannot prevent this rapid activity of intrusions. However, taking the different approach of using a proactive, behavioral-based system can identify and dynamically prevent malicious code from interacting with a host system and therefore can prevent known and unknown (day-zero) attacks.
The most effective way to provide endpoint security is to use a signatureless approach that does not require updates or patches and yet provides a proactive mechanism to protect the host against both known and unknown (day-zero) vulnerabilities, intrusions, and attacks.