Denial-of-service (DoS) attacks and distributed denial-of-service (DDoS) attacks have become more sophisticated and prevalent over the years and are therefore major issues in service provider and large-scale network deployments.
In today's rapidly evolving networks, attackers are often one step ahead. Effective mitigation of DDoS attacks is a pressing problem. Proactive detection and prevention mechanisms can help protect the network from these malicious cloaking techniques.
The Cisco Anomaly Detection and Mitigation solution provides a self-defending preventive solution for detecting and mitigating complex and sophisticated DoS and DDoS attacks.
This chapter provides the details of the Anomaly Detection and Mitigation solution that uses the industry standard Cisco Traffic Anomaly Detectors and Cisco Guard DDoS Mitigation devices. The chapter takes a closer look at core concepts, solution architecture, solution components, and how all these are combined to demonstrate how the solution works through various illustrations and diagrams.
The chapter provides a brief overview of the configuring and managing of the Cisco Traffic Anomaly Detector and Cisco Guard Mitigation devices, showing sample configurations that use a command-line interface (CLI) and defining how to configure Zones, Filters, Policies, Learning Process parameters, and how to activate the Anomaly Detection and the Guard system.
The main objective of any DoS and DDoS attacks is to prevent authorized users from accessing network resources.
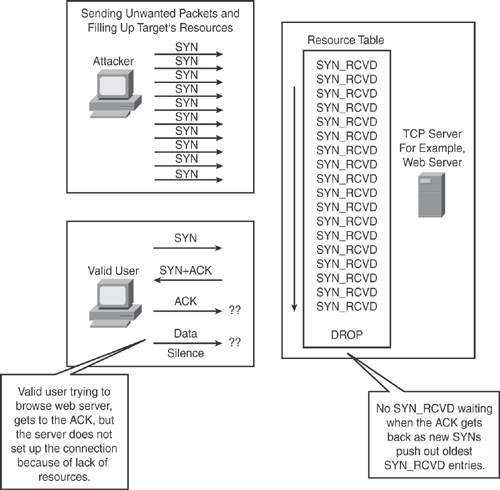
The main objective of a DoS-type attack is to prevent access to authorized users by consuming the resources such as bandwidth, memory, storage, and CPU. The attacker floods the target host(s) with unwanted packets and uses up all the resources, thus crippling the network and saturating network links, resulting in regular traffic either being slowed down, disrupted for some period, or completely interrupted.
Typically, a DoS attack is an attempt to disrupt services and prevent legitimate users from accessing certain information or services. For example, a DoS attack can be launched to prevent legitimate users from accessing e-mail, browsing Internet websites, printing services, or preventing access to any local network resources. Examples of DoS attacks include but are not limited to
Resource removal
Resource modification
Resource saturation
Figure 22-1 illustrates a basic form of DoS attack showing resource saturation in which an attacker is sending a large number of unwanted TCP SYN packets, thereby filling up the target server resources, thus preventing legitimate users from establishing a valid TCP connection.
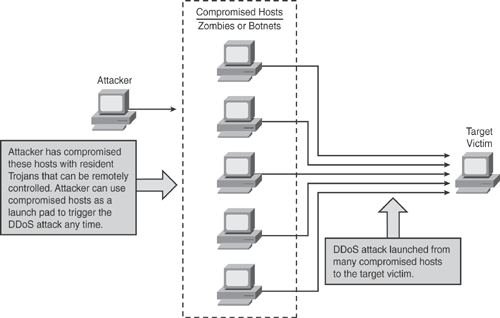
The objective of DDoS is similar to DoS; the major difference is that the attacker does not directly launch the attack to the target. In DDoS, the attacker compromises a multitude of systems by exploiting the security vulnerabilities and weaknesses within the systems and infects those systems with a resident Trojan, so that the attacker can take control of all compromised systems remotely.
After the compromised hosts are infected with a Trojan and ready for the attacker to use, the attacker uses them as a launch pad by sending huge amounts of unwanted traffic to the target host, thus creating a DDoS effect. This type of attack is called "distributed" because the attacker is using multiple hosts to launch the DoS attack on a single host or multiple host systems.
In DDoS, the attacker hides behind the compromised hosts, and the target victim is blindfolded so it cannot recognize the real perpetrator.
Victims of a DDoS attack consist of both the end targeted system and all systems maliciously used and controlled by the attacker in the distributed attack.
DDoS type attacks are harder to track down than DoS attacks, and they challenge defense mechanisms.
Figure 22-2 illustrates a basic form of DDoS attack in which an attacker has compromised multiple hosts with resident Trojans, thereby allowing the hosts to be remotely controlled. The attacker can use compromised hosts as a launch pad to trigger the DDoS attack to the target victims, thus preventing legitimate users from establishing connections.