As mentioned earlier, the Cisco Traffic Anomaly Detector device works in combination with the Cisco Guard Mitigation device to provide a comprehensive anomaly protection against DDoS attacks.
Figures 22-6 through 22-10 illustrate the combination of the Cisco DDoS solution and the dynamic diversion solution.
The following steps highlight each step of the anomaly detection and mitigation process during an attack life cycle in reference to Figures 22-6 through 22-10.
Note
It is assumed that the Traffic Anomaly Detector and the Guard Mitigation device have both completed the learning process, classifying and categorizing the normal zone traffic pattern using an algorithm-based process to establish a baseline.
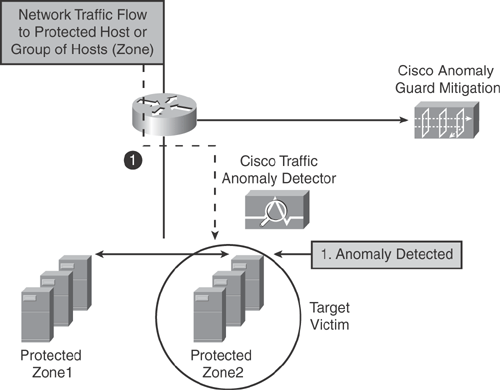
Step 1. | As illustrated in Figure 22-6, the Traffic Anomaly Detector device is deployed closer to the protected zone to detect anomalies and provide detection and alerting capabilities. Normal traffic flow is moving to Zone1 and Zone2 servers. The Traffic Anomaly Detector device identifies an anomaly in Zone2 and has detected an intrusion that deviates from the normal traffic policy. |
Step 2. | As illustrated in Figure 22-7, the Traffic Anomaly Detector device alerts the Cisco Guard Mitigation device to begin dynamic diversion, which redirects traffic destined for the targeted resources, and provides traffic flow information of the intrusion detected. This can either be triggered manually or automatically. Figure 22-7. Step 2—Cisco Traffic Detector Alerts Cisco Guard
|
Step 3. | As illustrated in Figure 22-8, the Cisco Guard Mitigation device triggers a redirection to the edge router for the target victim's traffic under suspicion to be redirected to the Guard. This can be achieved via routing protocol and Border Gateway Protocol (BGP) updates. All other traffic continues to flow directly to its designated destinations without interruption. Only the target victim traffic is redirected to the Guard. Figure 22-8. Step 3—Cisco Guard Triggers Traffic Diversion
|
Step 4. | As illustrated in Figure 22-9, the edge router is now diverting all target victims' traffic (only) to the Cisco Guard Mitigation device for scrubbing. The diverted traffic is then scrutinized to classify and separate bad flows from legitimate flows filtering malicious data. The Guard performs detailed flow-level analysis to identify and mitigate the attack. Figure 22-9. Step 4 —Diverted Traffic Is Redirected to Cisco Guard for Scrubbing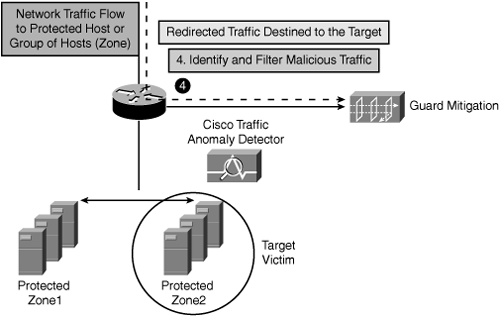
|
Step 5. | As illustrated in Figure 22-10, the Guard filters and blocks all malicious attack traffic and forwards all legitimate traffic to its designated destination, ensuring uninterrupted network flow for valid users and legitimate transactions. Figure 22-10. Step 5 —Cisco Guard Forwards Legitimate Traffic to Original DestinationThe information concept in Figures 22-6 to 22-10 is compiled from the Cisco Networkers session presentation BRKSEC-2030 on "Deploying Network IPS."
|