Today, organizations face increased pressure to comply with an array of industry regulations and legislations. Corporate governance must enforce effective controls and manage confidentiality and integrity of information. Organizations can face heavy penalties and can cause severe damage to the corporate image if they experience security breaches or are found out of compliance.
The chapter focuses on managing an effective organizational security model that provides a total security framework that includes policy compliance and risk mitigation. It provides details of various integrated pieces of the security model: security policies, industry standards, procedures, and guidelines.
This chapter highlights the two most widely used frameworks for industry best practices that are commonly employed by organizations for IT and corporate governance and for security audit compliance requirements—namely, ISO/IEC 17799 and COBIT.
In the process of reviewing the two commonly used best practices, the chapter provides details for some of the important regulatory compliance requirements, including the Gramm-Leach-Bliley Act (GLBA), HIPAA, and Sarbanes-Oxley Act (SOX) legislation, which are enforced in different types of businesses.
The chapter highlights how Cisco solutions and products help address the regulator compliance requirements and summarizes the value of the Cisco Self-Defending Network solution that is used in managing security risks and compliance.
A security model is a framework made of many integrated entities, including logical and physical protection mechanisms, all working together to provide secure systems that comply with industry best practices and regulations.
Understanding the value of information is the first step in the development of a security model. Managing security risk and compliance audit requirements demands a policy- and system-based approach. Network and network security are fundamental elements of building a security model for business governance and compliance.
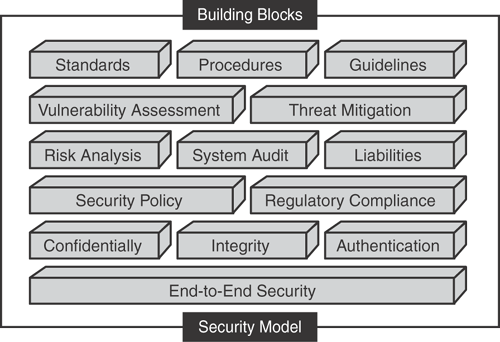
Figure 25-1 illustrates a high-level overview of the different layers in a security model that can be used as a basic template and guideline to achieve secure IT infrastructure.
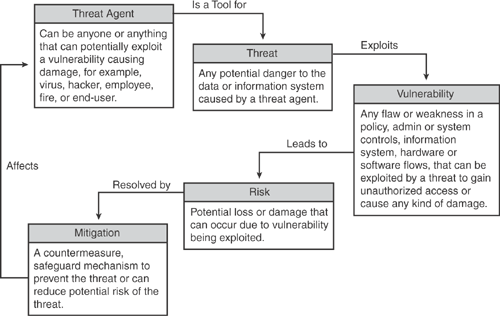
Often, security component terms are used interchangeably, although they carry different meanings in the context of different security components.
Figure 25-2 illustrates various security component associations and their relationships in the context of security framework.