Protecting and securing the information system has a fundamentally important role to play in business governance and regulatory compliance. Senior management is responsible for achieving this and providing comprehensive support for protecting information systems. This requires a complete understanding of what needs to be protected (assets) and the implications of failure (not meeting regulations).
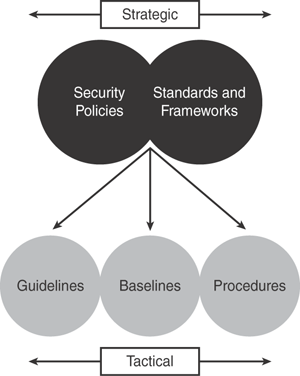
Management needs to define a security program to fulfill this obligation by establishing appropriate security policies, following industry standards, and establishing guidelines and detailed procedures to protect the organization.
A security policy is a high-level document—a set of general rules, principles, and practices established by the senior management within the organization.
A security policy can comprise varying sets of rules and statements that regulate how the organization will manage, protect, and distribute sensitive information and determine how security is implemented within the organization.
Security policies are strategically defined primary frameworks that can dictate and establish the needed levels of information security to achieve the desired confidentiality goals.
Security policies can be broadly categorized into three types:
Regulatory policies: Mandatory enforcements of compliance with industry regulations and legislations. These are typically driven to ensure that the organization is following industry standards as regulated by law.
Advisory policies: These drive confidentiality and integrity of information systems and outline the noncompliance ramifications.
Informative policies: These are non-enforceable and provide generic guidelines for best practices and acceptable behaviors.
Standards are industry-recognized best-practice frameworks and are agreed-upon principles of concepts and designs to implement, achieve, and maintain the required levels of processes and procedures.
Like security policies, standards are strategic in nature in that they define system parameters and processes.
Several available industry standards are used for various purposes. In the context of security information management and regulatory compliance, there are two notable standards—ISO 17799 and COBIT. These are discussed in the next sections.
Guidelines are recommended actions and operational guides for users. Similar to standards, guidelines are also tactical in nature. The major difference between standards and guidelines is that guidelines can be used as references, whereas standards are mandatory.
Procedures are low-level documents providing systematic step-by-step instructions on completing or fulfilling a certain task. Procedures are detailed in nature to provide maximum information to users to successfully implement and enforce the security policy and apply the standards and guidelines.
Figure 25-3 depicts the relationship between security policies, standards, guidelines, and procedures.