| |||
| |||
| |||
| |||
| |||
| |||
| |||
At the same time networks are growing exponentially, they are becoming complex and mission critical, bringing new challenges to those who run and manage them. The need for integrated network infrastructure comprising voice, video, and data (all-in-one) services is evident, but these rapidly growing technologies introduce fresh security concerns. Therefore, as network managers struggle to include the latest technology in their network infrastructure, network security has become a pivotal function in building and maintaining today's modern high-growth networks.
This chapter presents a broad description of network security in the context of today's rapidly changing network environments. The security paradigm is changing, and security solutions today are solution driven and designed to meet the requirements of business. To help you face the complexities of managing a modern network, this chapter discusses the core principles of security—the CIA triad: confidentiality, integrity, and availability.
In addition to discussing CIA, this chapter discusses security policies that are the heart of all network security implementations. The discussion covers the following aspects of security policies: standards, procedures, baselines, guidelines, and various security models.
The chapter takes a closer look at the perimeter security issue and the multilayered perimeter approach. The chapter concludes with the Cisco security wheel paradigm involving five cyclical steps.
When you are planning, designing, or implementing a network or are assigned to operate and manage one, it is useful to ask yourself the following questions:
What are your business objectives?
What do you need to accomplish these objectives?
What technologies or solutions are required to support these objectives?
Are your objectives compatible with your security infrastructure, operations, and tools?
What are the implications of not implementing security?
You can use these questions to pose and answer some of the basic questions that underlie fundamental requirements for establishing a secure network. Network security technologies reduce risk and provide a foundation for expanding businesses with intranet, extranet, and electronic commerce applications.
Solutions also protect sensitive data and corporate resources from intrusion and corruption.
Advanced technologies now offer opportunities for small and medium-sized businesses (SMB), as well as enterprise and large-scale networks to grow and compete; they also highlight a need to protect computer systems against a wide range of security threats.
The challenge of keeping your network infrastructure secure has never been greater or more crucial to your business. Despite considerable investments in information security, organizations continue to be afflicted by cyber incidents. At the same time, management aims for greater results with fewer resources. Hence, improving security effectiveness remains vital, if not essential, while enhancement of both effectiveness and flexibility has also become a primary objective.
Without proper safeguards, every part of a network is vulnerable to a security breach or unauthorized activity from intruders, competitors, or even employees. Many of the organizations that manage their own internal network security and use the Internet for more than just sending/receiving e-mails experience a network attack—and more than half of these companies do not even know they were attacked. Smaller companies are often complacent, having gained a false sense of security. They usually react to the last virus or the most recent defacing of their website. But they are trapped in a situation where they do not have the necessary time and resources to spend on security.
To cope with these problems, Cisco has developed the SAFE Blueprint, a comprehensive security plan that recommends and explains specific security solutions for different elements of networks.
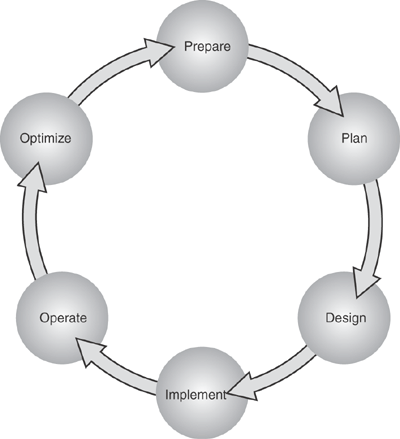
Cisco also offers the integrated security solution, which delivers services above and beyond the "one size fits all" model. In addition, Cisco services are designed to deliver value throughout the entire network life cycle that includes the stages of prepare, plan, design, implement, operate, and optimize (PPDIOO). the Cisco PPDIOO model, as shown in Figure 1-1, encompasses all the steps from network vision to optimization, enabling Cisco to provide a broader portfolio of support and end-to-end solutions to its customers.