Several new enhancements and advanced capabilities have been added in the IOS Firewall feature set in IOS Software 12.3T and 12.4 mainline versions. The following section highlights some of the commonly used advanced features.
The HTTP inspection engine in the IOS Firewall has been enhanced with the introduction of Advanced Application Inspection and Control. For HTTP port 80 web traffic passing through the conventional firewalls, there is a possibility that non-HTTP traffic can be embedded or tunneled in the HTTP traffic (for example, Instant Messaging (IM) or any malicious traffic), thereby bypassing the firewall. Using this embedding technique, malformed packets can be crafted to carry viruses, worms, Trojans, or any other malicious activity. With deep packet inspection, IOS Firewall inspects the data streams to ensure that traffic that is assumed to be HTTP is legitimate web browsing and not IM or illegitimate traffic that is trying to gain unauthorized access through the firewall.
As shown in Figure 5-5, the HTTP Inspection Engine gives IOS Firewall engine more granular control and the intelligence to block non-HTTP traffic by challenging its legitimacy and conformance to standards. The HTTP inspection performs packet inspection to detect whether any applications are being tunneled through port 80.
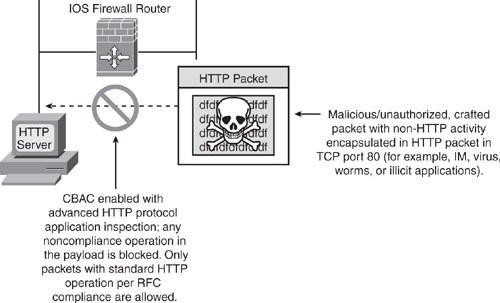
Packets not conforming to the standards in HTTP protocol are dropped. A reset message is sent out, and a SYSLOG message is generated accordingly.
This feature was introduced in IOS Version 12.3(14)T.
Note
For a configuration template, visit www.cisco.com/en/US/products/ps6350/products_configuration_guide_chapter09186a0080455927.html#wp1027188.
Similar to the SMTP protocol, the ESMTP protocol provides a basic method for exchanging e-mail messages. ESMTP specifies service extensions to the original SMTP protocol for sending e-mail messages that support graphics, audio, and video files, and text in various national languages. Although an ESMTP session is similar to SMTP, there is one difference—the EHLO command. An ESMTP client supporting ESMTP protocol starts a connection by issuing the EHLO command instead of the HELO command used in standard SMTP. (Refer to RFC 1869, "SMTP Service Extensions," for further details.)
The enhanced SMTP inspection engine adds support for ESMTP, Post Office Protocol 3 (POP3), and Internet Message Access Protocol (IMAP) in addition to the standard SMTP protocol. Advanced application inspection prevents protocol masquerading and enforcing strict RFC compliance.
To configure SMTP/ESMTP inspection, use the ip inspect name inspection-name {smtp | esmtp} command from the global configuration mode along with other required parameters. (Refer to steps defined earlier in the section "Configuring CBAC.") This feature was introduced in IOS Version 12.3(14)T.
Before the implementation of the Firewall ACL Bypass feature, a packet was subject to processing for three searches (inbound ACL, outbound ACL, and the session table of the firewall). As discussed earlier, the dynamic ACL entry is a result of the corresponding connection information found in the session table that validates the session as being legitimate; therefore, checking the packet against the inbound and outbound ACL entries was deemed redundant and no longer necessary. The extra checks can be eliminated to save CPU cycles. Bypassing the ACL check enhancement subjects the packet to one search only (the session table) during the packet processing path through the router. Figure 5-6 shows how this works. The primary benefit in this feature is that the performance of the packet throughput is improved by approximately 10%.
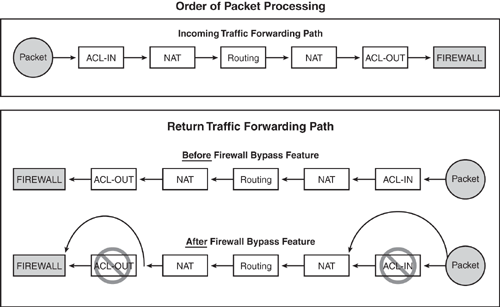
Because the firewall ACL bypassing is performed by default, you can configure CBAC inspection as normal. This feature is transparent to the user, and no additional commands are required to enable or disable it.
This feature was introduced in IOS Version 12.3(4)T.
The transparent IOS Firewall feature (also known as Layer 2 firewall) acts as a Layer 2 transparent bridge with CBAC inspection configured on the Bridged Virtual Interface (BVI).
A Layer 3 IOS Firewall implementation requires two logical zones—trusted and untrusted—both on different IP subnets (existing subnets). A network implementation not designed to accommodate this subnetted architecture would require the redesign of IP subnets to accommodate the firewall. Placing a Layer 3 firewall would be difficult in such scenarios and is considered resource intensive and could be unfeasible for most deployment scenarios.
Traditional firewalls operate in either a Layer 3 or Layer 2 (transparent) mode. The Cisco IOS Firewall is designed to simultaneously interoperate in both modes, providing scalability and ease of integration. This enhanced functionality allows a Cisco IOS Firewall to be implemented concurrently for both the Layer 2 transparent firewall operating on the bridged packets and a Layer 3 firewall operating on routed packets on the same device.
The transparent firewall configuration is no different from the Layer 3 firewall using the ip inspect command from the global configuration mode. The CBAC inspection rule ip inspect in/out command is applied to the bridged interfaces for Layer 2 protection, whereas other routed interfaces are configured for Layer 3 protection.
This feature was introduced in IOS Version 12.3(7)T.
Before the implementation of the Virtual Fragmentation Reassembly (VFR) feature, the IOS Firewall (CBAC) could not identify the contents of the IP fragments or gather any port information from the fragmented packets. This shortcoming allowed all fragmented packets to bypass the firewall checks and get through the network without being inspected.
Before the VFR feature was available, several known fragment-type attacks could succeed. (Examples include Tiny Fragment attack, Overlapping Fragment attack, and the Buffer Overflow attack that sends a large number of incomplete IP fragments to thwart the firewall.) The VFR feature provides the capability to scan into the fragmented packets to check the connection information and create the corresponding dynamic ACL entries, hence protecting the network from various fragmentation attacks.
To enable VFR, use the ip virtual-reassembly command from the interface configuration mode. Example 5-6 shows how to configure VFR with a maximum number of 100 IP datagrams to be reassembled at any given time and a maximum number of 20 fragments allowed per IP datagram (fragment set). The timeout of 5 seconds specifies that if all the fragment packets are not received within the specified time, the IP datagram and all its fragments will be dropped.
This feature was introduced in IOS Version 12.3(8)T.
interface Fastethernet0/0
ip inspect <name> in | out
ip virtual-reassembly max-reassemblies 100 max-fragments 20 timeout 5
! |
The Multiprotocol Label Switching Virtual Private Network (MPLS VPN) feature allows several sites to interconnect transparently through a service provider network. A service provider network can support several IP VPNs. Each of these appears as a separate private network. VRF is an IP routing table instance for connecting sites in a VPN network. Each VPN has its own set or sets of VRF instances, thereby allowing each site to send IP packets to any other site in the same VRF instance.
The Cisco IOS Firewall feature is enhanced to support inspection for VRF instances in a MPLS VPN network. CBAC can inspect packets on a per-VRF basis for packets sent and received within a VRF. VRF-aware CBAC implementation can include multiple firewall instances (with VRF instances) that are allocated to separate VPN customers. VRF-aware CBAC provides scalability and low-cost integration without the need for separate firewall devices for each VPN network. In effect, a single physical router running multiple virtual routing instances (emulating multiple routers) can now run multiple virtual IOS Firewalls in a single device.
This feature was introduced in IOS Version 12.3(14)T.
The Cisco IOS Firewall feature is enhanced to support inspection for traffic that was originated by or destined to the CBAC-configured device. Inspection of router-generated traffic augments CBAC functionality to inspect TCP, UDP, and H.323 connections that have the firewall as one of the connection endpoints. CBAC dynamically opens temporary holes for TCP, UDP, and H.323 control channel connections to and from the router, and for the data and media channels negotiated over the H.323 control channels. For example, CBAC can be configured to inspect a Telnet initiated from the CBAC-enabled router to a device in the unprotected zone, allowing return traffic dynamically without needing to explicitly permit in the access list.
To enable the Router-Generated Traffic inspection feature, use the router-traffic keyword in the ip inspect name command when configuring CBAC inspection rules. This option is available for H.323, TCP, and UDP protocols only.