This section provides configuration examples to enable an 802.1x authentication mechanism on Cisco Catalyst switches that are running Cisco IOS and Cisco Aironet Wireless LAN Access Points running Cisco IOS.
Example 11-1 shows how to enable port-based 802.1x and RADIUS configuration on a Cisco Catalyst switch running Cisco IOS as depicted in Figure 11-4. The example also shows how to enable AAA authentication and RADIUS configuration, including the optional authorization for all network-related service requests, such as per-user ACLs, quotas, and VLAN assignment. The example also shows how to enable optional functionality or change default parameters. For example, periodic reauthentication is enabled, guest VLAN assignment is set to VLAN 10, and maximum number of times that the switch sends an EAP-request to the client is set to 3 (assuming no response is received) before restarting the authentication process.
hostname switch ! aaa new-model aaa authentication dot1x default group radius aaa authorization network default group radius ! dot1x system-auth-control ! interface FastEthernet 0/1 switchport mode access dot1x pae authenticator dot1x port-control auto dot1x max-req 3 dot1x reauthentication dot1x guest-vlan 10 ! radius-server host 10.1.1.5 key cisco ! |
Note
It is important to understand the AAA implementation and the consequences of adding the AAA commands to the Cisco IOS configuration, because they affect device access (vty and Console lines) as well. For example, by adding the AAA commands as shown in the previous example, Telnet access is restricted unless the appropriate user accounts and privilege levels are added on the RADIUS server or use separate named method lists with no authentication or line authentication for device access, which are applied to VTY and Console lines only. Refer to Chapter 8, "Securing Management Access," for configuration examples and explanation on AAA default method and named method lists.
This section continues the discussion of using switches as authenticators, as presented in the earlier section on the wireless LAN (multipoint) section and shown in Figure 11-6. When using an AP that is noncompliant and does not support the 802.1x authentication, the switch can act as the authenticator and authenticate the indirectly attached wireless clients.
The switch needs one additional command to support the multiple host scenario, which was explained in the section "Wireless LAN (Multipoint)" and depicted in Figure 11-6. Configure the dot1x host-mode multi-host command under the interface configuration mode, and in addition use the dot1x port-control auto command:
Switch(config)# interface FastEthernet 0/1 Switch(config-if)# dot1x port-control auto Switch(config-if)# dot1x host-mode multi-host
AAA authorization must be configured on the authenticator if network-related services such as per-user VLAN assignment on 802.1x authenticated ports are required. The following vendor-specific tunnel attributes need to be configured on the RADIUS server to be passed down to the authenticator. AAA authorization must be configured for this to work, as previously shown in Example 11-1.
Two types of RADIUS server selections available in Cisco Secure ACS can be selected to achieve this purpose, and both can be used when defining the authenticator (switch or AP) as the AAA client in the network configuration on Cisco Secure ACS:
RADIUS (IETF)
When the RADIUS (IETF) server is selected as the NAS type in Cisco Secure ACS, the following three attributes (attribute 64, 65, and 81) must be returned to the switch for 802.1x authentication:
- [RADIUS Attribute 64] Tunnel-Type = VLAN. RADIUS attribute [64] must contain the value "VLAN" (type 13).
- [RADIUS Attribute 65] Tunnel-Medium-Type = 802. Attribute [65] must contain the value "802" (type 6).
- [RADIUS Attribute 81] Tunnel-Private-Group-ID = VLAN NAME. Attribute [81] contains the VLAN name or VLAN ID assigned to the authenticated user.
RADIUS (Cisco IOS/PIX 6.0)
When RADIUS (Cisco IOS/PIX 6.0) server is selected as the NAS type in Cisco Secure ACS, the vendor-specific AV-Pair (Attribute 26) must be used to download attribute 64, 65, and 81, to be returned to the switch for 802.1x authentication:
[RADIUS Attribute 26] Vendor Specific Attribute (VSA)
- cisco-avpair= "tunnel-type(#64)=VLAN(13)"
- cisco-avpair= "tunnel-medium-type(#65)=802 media(6)"
- cisco-avpair= "tunnel-private-group-ID(#81)=vlan_name or vlan_id"
Figure 11-7 and Figure 11-8 show screenshots from Cisco Secure ACS that illustrate configuring RADIUS attributes for the two types of RADIUS server selection: RADIUS (IETF) and RADIUS (Cisco IOS/PIX 6.0).
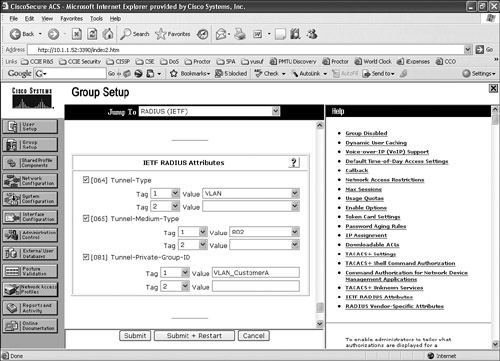
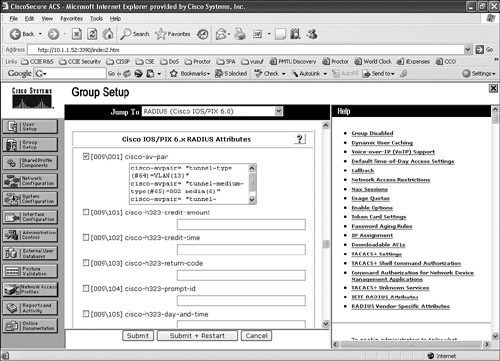
To verify that the RADIUS authorization is passing the correct attributes back to the authenticator (switch), enable debug radius on the Cisco IOS device and run the test aaa command to verify that the RADIUS is sending the required 802.1x attributes (attributes 64, 65, and 81).
The output in Example 11-2 shows the RADIUS (IETF) type server sending the three attributes (attributes 64, 65, and 81) from the ACS server.
|
Code View: Switch# debug radius Switch# show debug Radius protocol debugging is on Radius packet protocol debugging is on ! Switch# test aaa group radius dot1xuser cisco legacy Attempting authentication test to server-group radius using radius User was successfully authenticated. 5d07h: RADIUS: Pick NAS IP for u=0x2080E58 tableid=0 cfg_addr=0.0.0.0 5d07h: RADIUS: ustruct sharecount=1 5d07h: Radius: radius_port_info() success=0 radius_nas_port=1 5d07h: RADIUS(00000000): Send Access-Request to 10.1.1.52:1645 id 1645/3, len 61 5d07h: RADIUS: authenticator 58 B0 5A F7 78 0A 52 62 - 15 04 F3 A3 D7 13 CE 96 5d07h: RADIUS: NAS-IP-Address [4] 6 10.1.1.1 5d07h: RADIUS: NAS-Port-Type [61] 6 Async [0] 5d07h: RADIUS: User-Name [1] 11 "dot1xuser" 5d07h: RADIUS: User-Password [2] 18 * 5d07h: RADIUS: Received from id 1645/3 10.1.1.52:1645, Access-Accept, len 83 5d07h: RADIUS: authenticator BF F7 C9 3B 87 EF 45 71 - 75 75 BB 51 A5 E0 0E 50 5d07h: RADIUS: Tunnel-Type [64] 6 01:VLAN [13] 5d07h: RADIUS: Tunnel-Medium-Type [65] 6 01:ALL_802 [6] 5d07h: RADIUS: Tunnel-Private-Group[81] 14 01:"VLAN_CustomerA" 5d07h: RADIUS: Framed-IP-Address [8] 6 255.255.255.255 5d07h: RADIUS: Class [25] 31 5d07h: RADIUS: 43 41 43 53 3A 30 2F 64 38 61 2F 63 61 30 32 30 [CACS:0/d8a/ca020] 5d07h: RADIUS: 31 30 66 2F 64 6F 74 31 78 75 73 65 72 [10f/dot1xuser] 5d07h: RADIUS: saved authorization data for user 2080E58 at 20CA108 |
The output in Example 11-3 shows the RADIUS (Cisco IOS/PIX 6.0) type server sending the same three attributes (attributes 64, 65, and 81) via the VSA attribute 26 from the ACS server.
|
Code View: Switch# debug radius Switch# show debug Radius protocol debugging is on Radius packet protocol debugging is on ! Switch# test aaa group radius dot1xuser cisco legacy Attempting authentication test to server-group radius using radius User was successfully authenticated. 5d07h: RADIUS: Pick NAS IP for u=0x2139538 tableid=0 cfg_addr=0.0.0.0 5d07h: RADIUS: ustruct sharecount=1 5d07h: Radius: radius_port_info() success=0 radius_nas_port=1 5d07h: RADIUS(00000000): Send Access-Request to 10.1.1.52:1645 id 1645/4, len 61 5d07h: RADIUS: authenticator 51 58 41 7D 90 6A D9 DA - 3C 59 75 F1 71 FC BE 11 5d07h: RADIUS: NAS-IP-Address [4] 6 10.1.1.1 5d07h: RADIUS: NAS-Port-Type [61] 6 Async [0] 5d07h: RADIUS: User-Name [1] 11 "dot1xuser" 5d07h: RADIUS: User-Password [2] 18 * 5d07h: RADIUS: Received from id 1645/4 10.1.1.52:1645, Access-Accept, len 256 5d07h: RADIUS: authenticator 87 FE 14 E1 4A 54 62 25 - F8 2C FC 4A C1 8C 33 B6 5d07h: RADIUS: Vendor, Cisco [26] 49 5d07h: RADIUS: Cisco AVpair [1] 43 "cisco-avpair= "tunnel- type(#64)=VLAN(13)"" 5d07h: RADIUS: Vendor, Cisco [26] 60 5d07h: RADIUS: Cisco AVpair [1] 54 "cisco-avpair= "tunnel-medium- type(#65)=802 media(6)"" 5d07h: RADIUS: Vendor, Cisco [26] 64 5d07h: RADIUS: Cisco AVpair [1] 58 "cisco-avpair= "tunnel-private-group- ID(#81)=VLAN_CustomerA"" 5d07h: RADIUS: Tunnel-Type [64] 6 01:VLAN [13] 5d07h: RADIUS: Tunnel-Medium-Type [65] 6 01:ALL_802 [6] 5d07h: RADIUS: Tunnel-Private-Group[81] 14 01:"VLAN_CustomerA" 5d07h: RADIUS: Framed-IP-Address [8] 6 255.255.255.255 5d07h: RADIUS: Class [25] 31 5d07h: RADIUS: 43 41 43 53 3A 30 2F 64 38 63 2F 63 61 30 32 30 [CACS:0/d8c/ca020] 5d07h: RADIUS: 31 30 66 2F 64 6F 74 31 78 75 73 65 72 [10f/dot1xuser] 5d07h: RADIUS: saved authorization data for user 2139538 at 2080EB0 |
Based on the 802.1x port configuration in Example 11-1 and the RADIUS attributes downloaded from the authentication server, Example 11-4 displays the show dot1x command being used to verify the dot1x interface on the switch. The output shows that the client has successfully passed the 802.1x authentication and the optional 802.1x parameters configured for the interface as per Example 11-1.
Switch# show dot1x interface FastEthernet 0/1 Supplicant MAC 0001.2a2f.0ac2 AuthSM State= AUTHENTICATED BendSM State= IDLE Posture = N/A PortStatus= AUTHORIZED MaxReq = 3 MaxAuthReq= 2 HostMode = Single PortContro= Auto ControlDirection= Both QuietPeriod= 60 Seconds Re-authentication = Enabled ReAuthPeriod= 3600 Seconds ServerTimeout= 30 Seconds SuppTimeout= 30 Seconds TxPeriod= 30 Seconds Guest-Vlan= 10 |
Example 11-5 shows how to enable port-based 802.1x and RADIUS configuration on a Cisco Aironet Wireless LAN Access Point running Cisco IOS.
aaa new-model ! aaa authentication login myeap group radius ! dot11 ssid cisco authentication open eap myeap authentication network-eap myeap ! interface Dot11Radio0 ssid cisco ! radius-server host 10.1.1.52 radius-server key cisco ! |
Note
A named authentication method list is used in Example 11-5 in the aaa authentication login command on the Cisco Aironet wireless LAN access point, instead of using the default method list. The SSID configuration submode requires a list name to be referenced with the authentication [open | network-eap] commands, as shown in Example 11-5.
Based on the 802.1x port configuration in Example 11-5, Example 11-6 shows how to verify the dot1x interface on the access point. The output shows that the client has successfully passed the 802.1x authentication.
ap# show dot11 associations
802.11 Client Stations on Dot11Radio0:
SSID [cisco] :
MAC Address IP addressDeviceNameParentState
0001.2a2f.0ac2 10.1.1.1 350-client sdelairselfEAP-Associated |
A supplicant client such as the Microsoft Windows XP operating system supports IEEE 802.1x authentication by default on all LAN-based network cards. By default, Windows XP uses the EAP-TLS authentication type; this can be changed to use another EAP method instead of the default EAP-TLS.
To configure a wireless network adapter for the IEEE 802.1X authentication on a client that is running Microsoft Windows XP, use the Authentication tab on the properties of the wireless network card, which is available from the Wireless Networks tab of the properties of a wireless connection in Network Connections.
For more details on configuring a wireless network adapter for the IEEE 802.1X authentication on a client running Microsoft Windows XP, refer to the following URL: http://tinyurl.com/28nvkt.